KeRanger, FileCoder, MacRansom, and EvilQuest are four separate ransomware families that have been identified by Microsoft as having an effect on Apple macOS systems.
Although these malware families are ancient, the Security Threat Intelligence team of the IT behemoth wrote in a study on Thursday that they “exemplify the variety of capabilities and harmful behaviour achievable on the platform.”
These ransomware families first spread through what the creator of Windows refers to as “user-assisted methods,” in which the victim downloads and sets up trojanized software.
It can additionally arrive as a second-stage payload dropped by malware that already resides on the infected host or as a component of a supply chain attack.
Regardless of the assault strategy used, the attacks follow a similar pattern in which threat actors use legitimate operating system capabilities and weaknesses to gain access to the computers and encrypt important files.
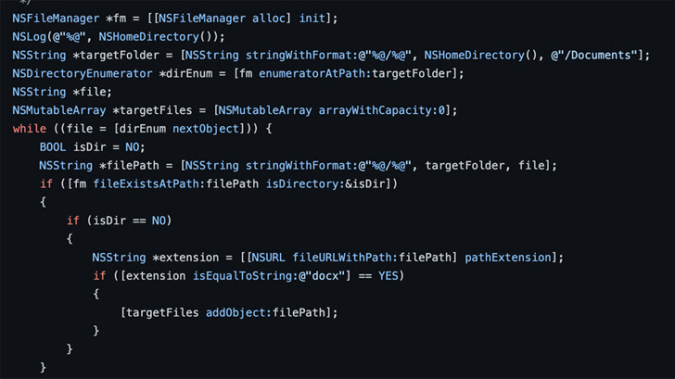
This involves listing files using library functions like opendir, readdir, and closedir as well as the Unix search programme. Microsoft mentioned another approach, but the ransomware strains did not use it: the NSFileManager Objective-C interface.
In an effort to thwart analysis and debugging efforts, malware such as KeRanger, MacRansom, and EvilQuest have also been seen to employ a combination of hardware- and software-based tests to establish whether the malware is operating in a virtual environment.
Notably, KeRanger uses the strategy of delayed execution to avoid discovery. After being launched, it sleeps for three days before resuming its destructive operations.
Launch agents and kernel queues are used to establish persistence, which is necessary to ensure that the malware is run even after a system restart, according to Microsoft.
While KeRanger uses AES encryption in cypher block chaining (CBC) mode to accomplish its objectives, FileCoder uses the ZIP programme to encrypt files. On the other hand, both MacRansom and EvilQuest use a symmetric encryption technique.
In addition to standard ransomware functions, EvilQuest, which was initially discovered in July 2020, also has trojan-like characteristics like keylogging, compromising Mach-O files by inserting arbitrary code, and deactivating security tools.
It also packs in capabilities to execute any file directly from memory, effectively leaving no trace of the payload on disk.
“Ransomware continues to be one of the most prevalent and impactful threats affecting organizations, with attackers constantly evolving their techniques and expanding their tradecraft to cast a wider net of potential targets,” Microsoft said.
Suggest an edit to this article
Check out our new Discord Cyber Awareness Server. Stay informed with CVE Alerts, Cybersecurity News & More!
Remember, CyberSecurity Starts With You!
- Globally, 30,000 websites are hacked daily.
- 64% of companies worldwide have experienced at least one form of a cyber attack.
- There were 20M breached records in March 2021.
- In 2020, ransomware cases grew by 150%.
- Email is responsible for around 94% of all malware.
- Every 39 seconds, there is a new attack somewhere on the web.
- An average of around 24,000 malicious mobile apps are blocked daily on the internet.




