Last week researchers found the critical vulnerability CVE-2022-22965 in Spring – the open source Java framework. Using the vulnerability, an attacker can execute arbitrary code on a remote web server, which makes CVE-2022-22965 a critical threat, given the Spring framework’s popularity. By analogy with the infamous Log4Shell threat, the vulnerability was named Spring4Shell.
CVE-2022-22965 and CVE-2022-22963: Technical Details
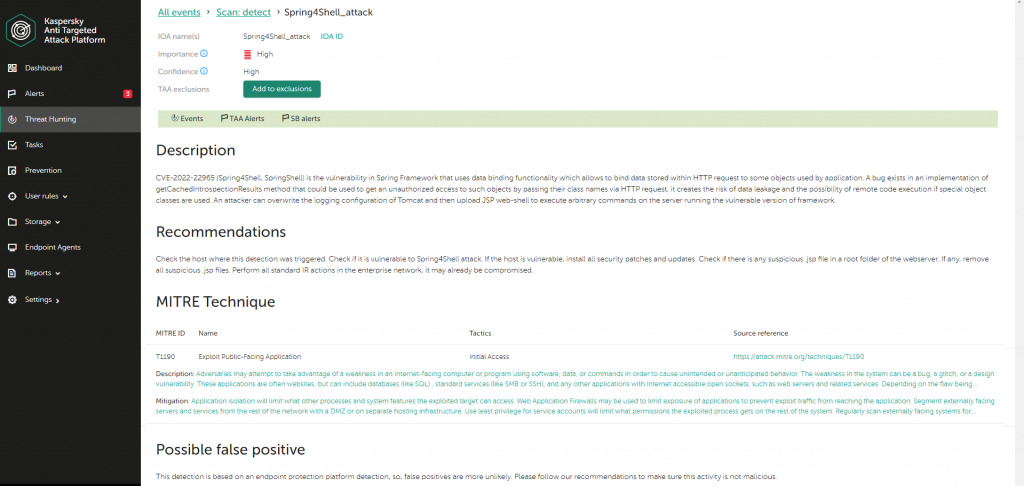
CVE-2022-22965 (Spring4Shell, SpringShell) is a vulnerability in the Spring Framework that uses data binding functionality to bind data stored within an HTTP request to certain objects used by an application. The bug exists in the getCachedIntrospectionResults method, which can be used to gain unauthorized access to such objects by passing their class names via an HTTP request. It creates the risks of data leakage and remote code execution when special object classes are used. This vulnerability is similar to the long-closed CVE-2010-1622, where class name checks were added as a fix so that the name did not match classLoader or protectionDomain. However, in a newer version of JDK an alternative method exists for such exploitation, for example, through Java 9 Platform Module System functionality.
So an attacker can overwrite the Tomcat logging configuration and then upload a JSP web shell to execute arbitrary commands on a server running a vulnerable version of the framework.
A typical vulnerable configuration consists of:
- JDK version 9+
- Apache Tomcat for serving the application
- Spring Framework versions 5.3.0 to 5.3.17 and 5.2.0 to 5.2.19 and below
- application built as a WAR file
CVE-2022-22963 is a vulnerability in the routing functionality of Spring Cloud Function that allows code injection through Spring Expression Language (SpEL) by adding a special spring.cloud.function.routing-expression header to an HTTP request. SpEL is a special expression language created for Spring Framework that supports queries and object graph management at runtime. This vulnerability can also be used for remote code execution.
A typical vulnerable configuration consists of:
- Spring Cloud Function 3.1.6, 3.2.2 and older versions
Mitigations for Spring vulnerabilities exploitation
CVE-2022-22965 is fixed in 2.6.6; see the Spring blog for details.
To fix CVE-2022-22963, you also need to install the new Spring Cloud Function versions; see the VMware website for details.
To detect exploitation attempts, ensure that Advanced Exploit Prevention and Network Attack Blocker features are enabled. Some techniques used during exploitation can be seen in other exploits that we detect, which is why the verdict names can differ.
Indicators of Compromise
Verdicts
PDM:Exploit.Win32.Generic
UMIDS:Intrusion.Generic.Agent.gen
MD5 hashes of the exploits
7e46801dd171bb5bf1771df1239d760c – shell.jsp (CVE-2022-22965)
3de4e174c2c8612aebb3adef10027679 – exploit.py (CVE-2022-22965)
Detection of the exploitation process with Kaspersky EDR Expert
Suggest an edit to this article
Go to Cybersecurity Knowledge Base
Got to the Latest Cybersecurity News
Stay informed of the latest Cybersecurity trends, threats and developments. Sign up for our Weekly Cybersecurity Newsletter Today.
Remember, CyberSecurity Starts With You!
- Globally, 30,000 websites are hacked daily.
- 64% of companies worldwide have experienced at least one form of a cyber attack.
- There were 20M breached records in March 2021.
- In 2020, ransomware cases grew by 150%.
- Email is responsible for around 94% of all malware.
- Every 39 seconds, there is a new attack somewhere on the web.
- An average of around 24,000 malicious mobile apps are blocked daily on the internet.




