Anonymous and its affiliate groups have sent 7 million text messages to Russian citizens about the war in Ukraine while another group has hacked 400+ security cameras in the country with anti-war messages.
Anonymous hacktivists are claiming to have hacked into hundreds of public surveillance cameras installed across Russia to post messages against the Russian president Vladimir Vladimirovich Putin and in support of Ukraine.
It is worth noting that the hacktivists originally announced the hack on March 7th however at the time of publishing this article, most targeted cameras were still compromised and displaying content left by the group.
Details of the Hack
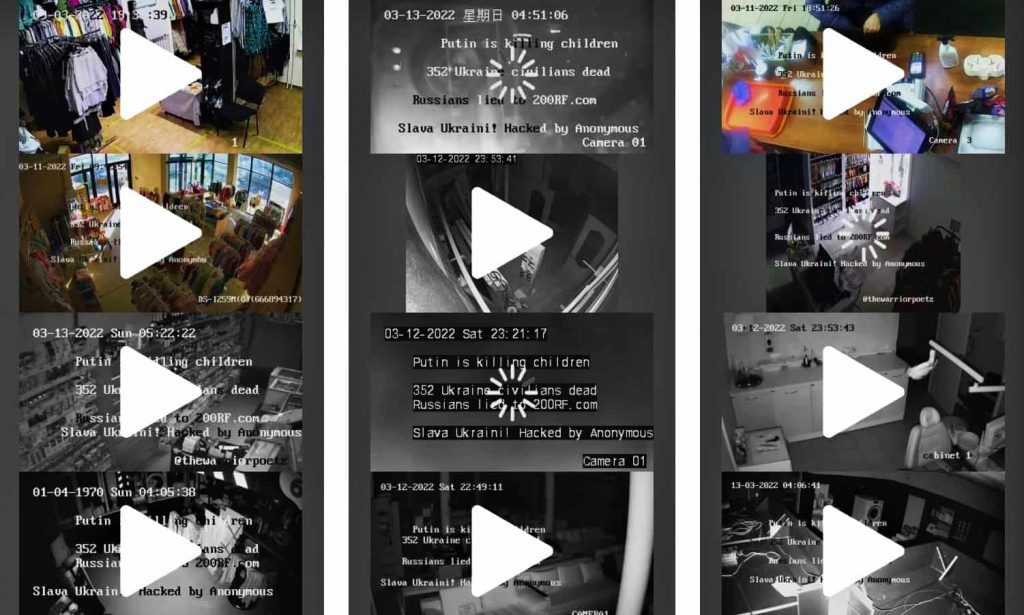
According to Anonymous, the group has compromised more than 400 security cameras in Russia and displayed anti-propaganda messages. The hacktivist collective has also compiled live feeds from 100+ Russian CCTV cameras and posted them on the newly launched website.
Apart from running live feeds of compromised security cameras; the website also explains why these cameras were hacked and how Anonymous supports Ukraine in the ongoing conflict between two countries.
The point of this leak is solely to spread information to the Russian people, and potentially (although unlikely) use these cameras for recon. Since most of these cameras are in deep Russia (and some near the border cities of Ukraine), this is mainly a large anti-propaganda movement. We are however working on cameras in Belarus, Ukraine, and closer to the Ukraine conflict in Russia, that will be used entirely for Recon for the Ukrainian military. That dump will come next.
Anonymous
Cameras Across multiple Sectors Hacked
The group claims it is trying to hack security cameras in Belarus, Ukraine, and regions closer to the Russian border and will use them to help the Ukrainian military conduct reconnaissance.
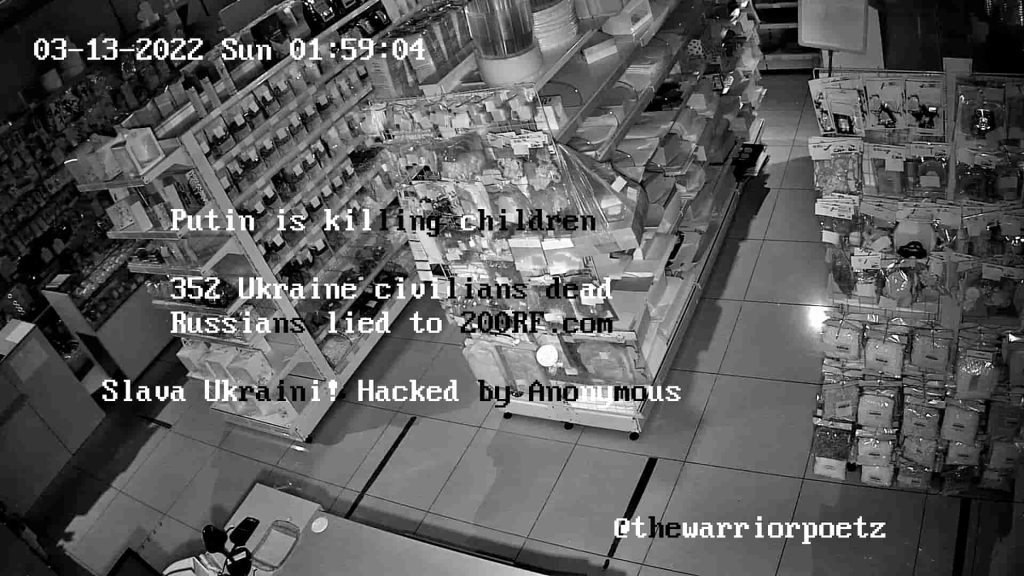
Anonymous has categorized the hacked cameras into Businesses, Outdoor, Indoor, Restaurants, Offices, Schools, and Security Offices, which explains the extensiveness of hacking. In most cases, Anonymous superimposed English text messages over live feeds such as the following:
For your information, the 200RF.com website is set up by Ukrainian Internal Affairs Ministry to allow Russian relatives to identify Russian soldiers who either captured or died during the war.
7 Million Text Messages Sent to Russians
In another incident, Squad303, a newly formed digital army comprising Anonymous-associated programmers, sent out over 7 million SMS messages to cell phone numbers across Russia.
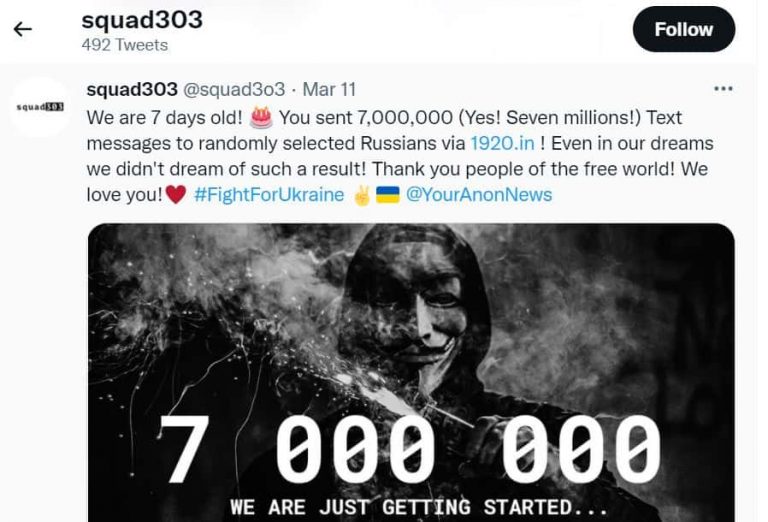
The group created a tool called 1920.in to allow non-technical individuals to contribute to #OpRussia, which is dubbed the world’s largest cyber operation to date. This campaign aimed to inform the Russian public about the war in Ukraine. Within 48 hours, the group sent out 2 million text messages, and by Tuesday, the SMS count reached 5 million.
In a video, Squad303 stated that they are trying to help Ukraine.
We have a message for the citizens of the free world: the legion is calling you. Ukraine needs you. You are the largest army in the history of the world. You don’t need any weapons or ammunition. Your weapons are smartphones and your ammo is messages sent to Russian citizens.
Anonymous – Squad303
Go to Cybersecurity Knowledge Base
Stay informed of the latest Cybersecurity trends, threats and developments. Sign up for RiSec Weekly Cybersecurity Newsletter Today
Remember, CyberSecurity Starts With You!
- Globally, 30,000 websites are hacked daily.
- 64% of companies worldwide have experienced at least one form of a cyber attack.
- There were 20M breached records in March 2021.
- In 2020, ransomware cases grew by 150%.
- Email is responsible for around 94% of all malware.
- Every 39 seconds, there is a new attack somewhere on the web.
- An average of around 24,000 malicious mobile apps are blocked daily on the internet.
Since the recent invasion by the Russian’s, the anonymous collective have been behind a large number of high-profile hacks and DDoS’s targeting Russian infrastructure. We expect this to continue. Here are some related articles.