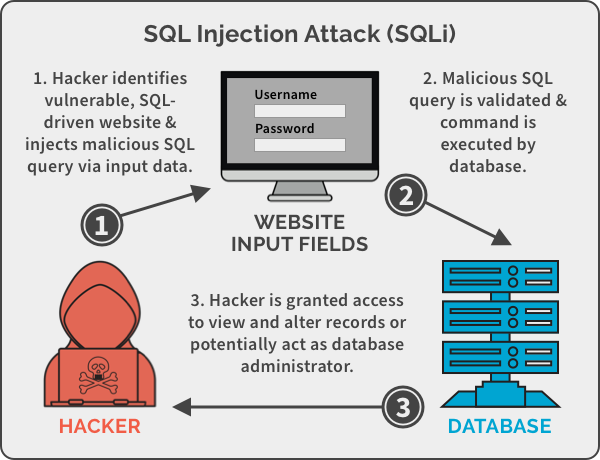
SpyCloud announced a report that examines trends related to exposed data. Researchers identified 1.7 billion exposed credentials, a 15% increase from 2020, and 13.8 billion recaptured Personally Identifiable Information (PII) records obtained from breaches in 2021.
Through its analysis of this data, it was found that despite increasingly sophisticated and targeted cyberattacks, consumers continue to engage in poor cyber practices regarding passwords, including the use of similar passwords for multiple accounts, weak or common passwords and passwords containing easy-to-guess words or phrases connected to pop culture.
“Reused passwords have been the leading vector in cyberattacks in recent years, and the threat of digital identity exposure is a growing problem,” said David Endler, Chief Product Officer of SpyCloud. “The findings of our annual report show that users are still not taking password security as seriously as they should. The threat of account takeover is not enacting wholesale improvements to consumer cyber hygiene, and that’s an alarming thought given the frequency of digital identity fraud.”
The average consumer owns hundreds of online accounts, each with a unique login, and the unfortunate result is an increase in consumer password reuse. SpyCloud’s report found that 64% of users with multiple compromised passwords reused similar passwords for multiple accounts, making them ripe for account takeovers and password spraying attacks. This represents a 4-point jump from the 2021 report.
The year over year increase in password reuse reflects the ease with which attackers can use one stolen password to compromise multiple accounts. More than 82% of the reused passwords analyzed consisted of an exact match to a previous password, and 70% of users tied to breaches last year and in years prior are still using an exposed password. Since 2016, SpyCloud has recaptured more than 25 billion total exposed accounts with passwords.
Strong correlation between current events and chosen passwords
In addition to reusing passwords for multiple accounts, the report identified a strong correlation between current events and chosen passwords. Report data showed passwords tied to numerous TV shows and movies in 2021, as well as pop and sports culture, including Britney Spears, the covislink pandemic and Major League Baseball World Series Champion the Atlanta Braves.
“The pandemic left many consumers with a longing for connection to society. In the same way consumers latched on to at-home entertainment via streaming services and sporting events, many reflected their hobbies in passwords from the previous year,” Endler said.
“The best defense to safeguard your company, customers and employees is to protect users from themselves by preventing them from selecting previously exposed passwords upon account creation or account password change, and monitoring for third party exposed credentials and resetting them as quickly as possible after an exposure.”
Compromised credentials – while a growing issue – is not the only threat outlined in this year’s report. Over the last 18 months SpyCloud researchers have increased their focus on bot logs from malware-infected devices which not only expose a user’s browser-saved passwords, but also detail browser fingerprints, web session cookies and other data that can allow criminals to impersonate a user’s online session and bypass two-factor authentication. This hard-to-detect fraud compounded with poor password hygiene can be a worrisome combo for even the most mature of security postures.
Many organizations and consumers think they’re protected from identity fraud through reliance on a dark web monitoring service. Unfortunately, it can take upwards of a year before compromised credentials make it to the dark web to be found by those services. By the time an organization or user receives an exposure notification, the damage is likely already done.
SpyCloud’s unique combination of human intelligence, technology and breadth of recaptured data allows organizations and users to proactively stop fraud transactions before they occur.
Additional findings
1,706,963,639 total exposed credentials were analyzed from 755 breach sources.
- The average breach contained 6,736,241 credentials.
- The government sector was heavily represented in 2021.
- SpyCloud found 611 breaches containing .gov email addresses – 81% of the overall total breach sources recaptured by SpyCloud.
- In total, the team found 561,753 credential pairs (email addresses and plaintext passwords) from government agencies internationally.
In addition to the more common types of data such as names, dates of birth, and national identification numbers or driver’s licenses, the exposure report uncovered vehicle makes and models, number of children, smoker status, marital status, estimated income, job title and even Reddit handles, specifically:
- 2.6 billion names
- 990 million addresses
- 393 million dates of birth
- 1.6 billion phone numbers
- 1.2 billion social media handles
12 notable recaptured data breaches of 2021.
- The March 2021 Park Mobile app breach (26 million records)
- The April 2021 Facebook user profiles scrape (501 million records)
- The April 2021 BigBasket breach (20 million records)
- The August 2021 T-Mobile breach (54 million records)
- The September 2021 Epik breach (15 million records)
Go to Cybersecurity Knowledge Base
Got to Cybersecurity News
Go to Homepage
Go to Cybersecurity Academy
Stay informed of the latest Cybersecurity trends, threats and developments. Sign up for RiSec Weekly Cybersecurity Newsletter Today
Remember, CyberSecurity Starts With You!
- Globally, 30,000 websites are hacked daily.
- 64% of companies worldwide have experienced at least one form of a cyber attack.
- There were 20M breached records in March 2021.
- In 2020, ransomware cases grew by 150%.
- Email is responsible for around 94% of all malware.
- Every 39 seconds, there is a new attack somewhere on the web.
- An average of around 24,000 malicious mobile apps are blocked daily on the internet.
Bookmark Please login to bookmarkClose