Ukraine has created what is described as an “IT army” to defend against Russian hackers and to launch counter operations against cyber threats.
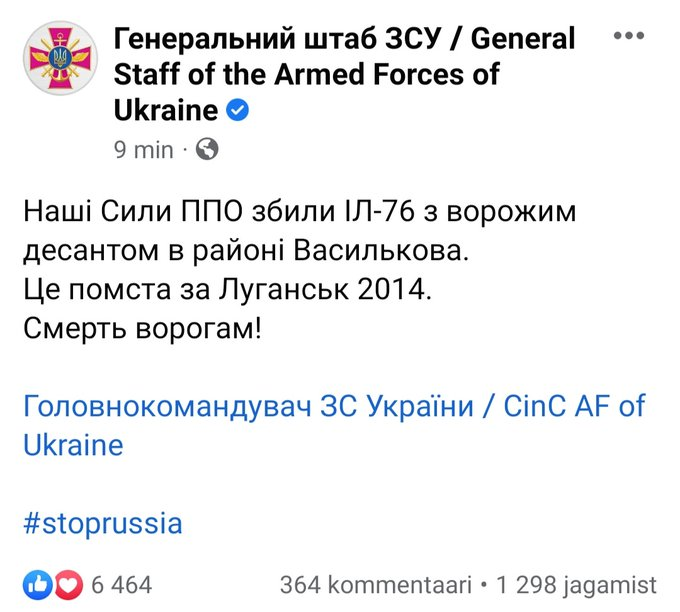
Russia’s invasion of Ukraine has been accompanied by cyberattacks targeting the country’s services and infrastructure, including DDoS attacks and destructive wiper malware campaigns – leading to the Ukrainian government calling for volunteers to aid with cybersecurity. But it has also asked for support in conducting offensive cyber operations back towards Russia.
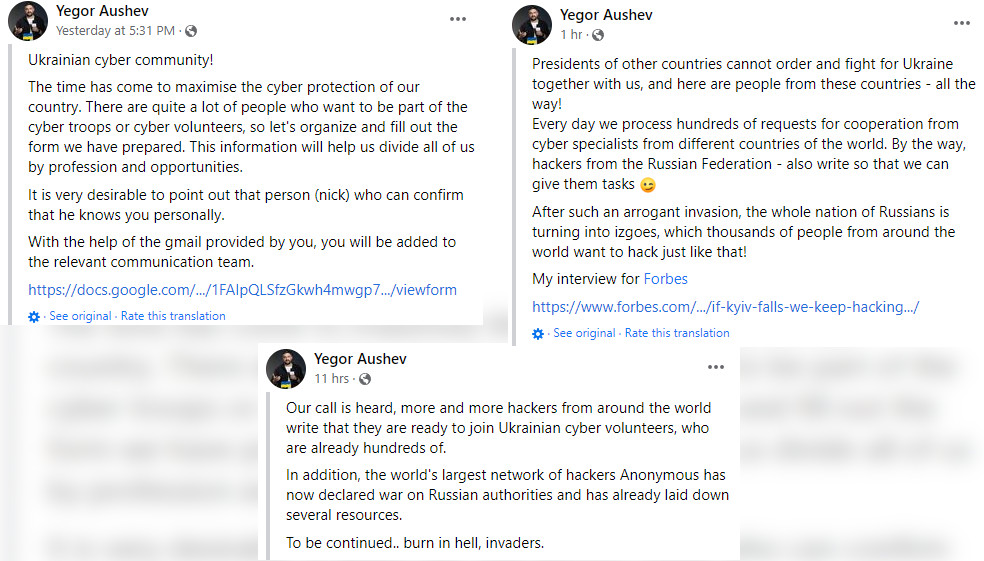
“We are creating an IT army,” Mykhailo Fedorov, vice prime minister of Ukraine said in a tweet at the weekend. “There will be tasks for everyone. We continue to fight on the cyber front. The first task is on the channel for cyber specialists,” he added, alongside a Telegram link to join the ‘IT Army of Ukraine’, which now has tens of thousands of subscribers.
In addition to helping to protect Ukrainian critical infrastructure and services from attacks, supporters were provided with a list of websites of 31 Russian targets.
They include organisations in both the state-backed and private sectors, including government agencies, banks, critical infrastructure and energy providers, including Gazprom and Lukoil, as well Russian email provider and search engine, Yandex. The list of targets is also being circulated in some underground forums.
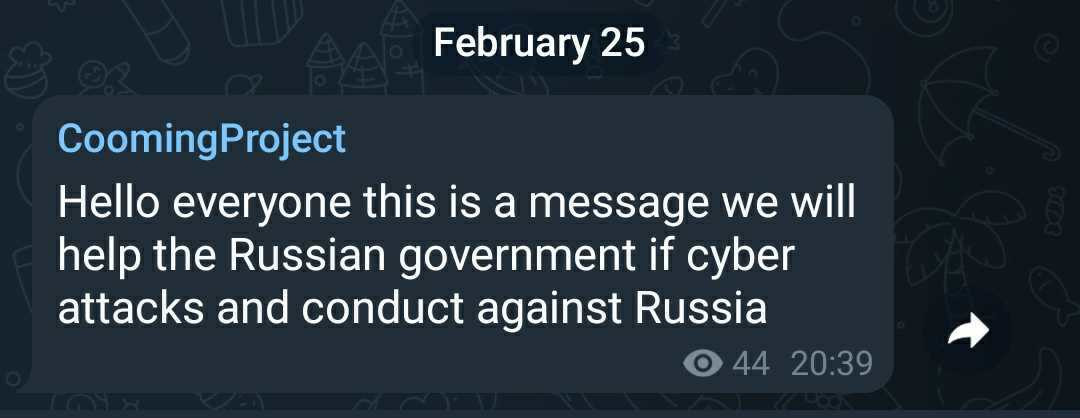
This IT army is just one of the online efforts taking place during the conflict; hacktivist collective Anonymous has said it is taking action in support of Ukraine and against Russia, while Russia-based cyber-criminal groups have also indicated that they’ll take offensive action in support of Vladimir Putin’s invasion.
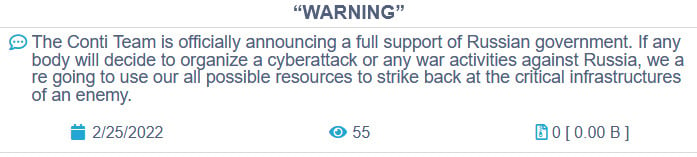
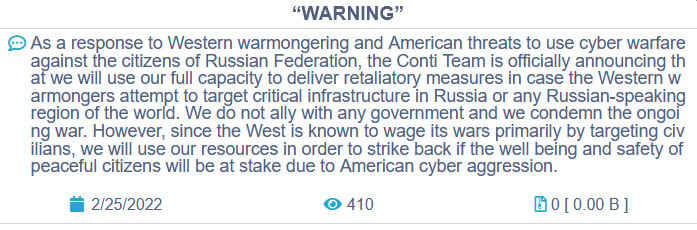
This includes the ransomware group Conti, which announced “full support of Russian government” and the intention to “strike back at the critical infrastructure of an enemy” in response to cyberattacks against Russia. A later statement by Conti claimed it doesn’t support any government, but it will strike back against the West and “American cyber aggression”. Conti has since seen many of its internal documents leaked in what appears to be another act of retaliation. Meanwhile, the BBC has also reported how Russian hackers – without direct orders from the state – are also attempting to hack Ukrainian websites and services.
According to analysis by Check Point, there’s a 196% increase in cyberattacks targeting Ukraine’s government and military since Russia sent troops in last week. It’s likely that cyberattacks will continue in both directions, particularly as more and more people join Ukraine’s cyber army.
“We’re now witnessing a concentrated attack to take down major websites and services in Russia and other surrounding countries, much like a community-driven effort. They have to deal with waves of DDoS attacks that are likely to worsen as time goes by,” says Silviu Stahie, a security analyst at Bitdefender.
It’s much too early to understand the impact of any of these developments. Something on the scale of Ukraine’s IT army has never been tried before, so it’s hard to know what kind of impact it will have, although it may play an important part simply in rallying support in broader terms.
There’s also the concern that civilians launching their own hacking attempts could have unexpected consequences. And the rise of offensive cyberattacks carried out by civilians raises a whole host of new questions – particularly as, in many countries, engaging in hacking is illegal.
“Conducting or participating in cyberattacks, even in what could be considered a noble effort to support Ukraine against the Russian aggression and invasion, could be subject to how different countries interpret hacking laws,” says Jens Monrad, head of threat intelligence, EMEA, at Mandiant.
“Another risk associated with this operation is how well each individual can protect themselves and how Russia might perceive it if they identify a foreign person suddenly hacking Russian targets,” says Monrad.
There’s also the risk that cyberattacks, intentionally or not, could cause disruption outside Ukraine and Russia.
As UK National Cyber Security Centre (NCSC) CEO Lindy Cameron commented recently: “Cyberattacks do not respect geographic boundaries”. International consensus also suggests the Russian military was behind the widespread and disruptive NotPetya malware attack of June 2017. The malware attack was designed to disrupt financial, energy and government sectors in Ukraine, but the malware spread to organisations around the world, costing an estimated billions of dollars in damages.
“As a combat veteran, I’m in total awe of the courage of the Ukrainian people. While there are no specific threats to the US, we must be prepared for spillover effects of Russian cyber ops or an uptick in ransomware,” Jen Easterly, director of the Cybersecurity and Infrastructure Security Agency (CISA), said on Twitter.
CISA, along with the UK’s NCSC, are among those cybersecurity agencies that have published advice on defending against cyber threats. In this environment, organisations around the world would be wise to examine their cybersecurity defences – because what comes next could be unpredictable.
Stay informed of the latest Cybersecurity trends, threats and developments. Sign up for RiSec Weekly Cybersecurity Newsletter Today
Remember, CyberSecurity Starts With You!
- Globally, 30,000 websites are hacked daily.
- 64% of companies worldwide have experienced at least one form of a cyber attack.
- There were 20M breached records in March 2021.
- In 2020, ransomware cases grew by 150%.
- Email is responsible for around 94% of all malware.
- Every 39 seconds, there is a new attack somewhere on the web.
- An average of around 24,000 malicious mobile apps are blocked daily on the internet.