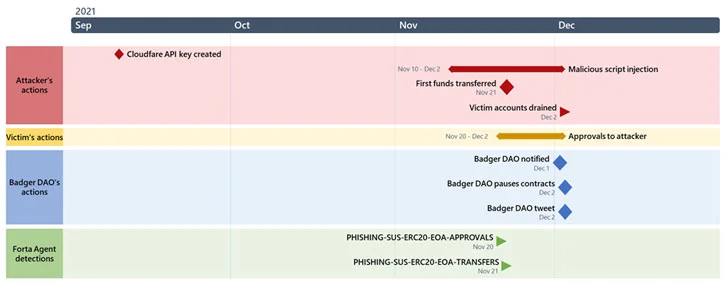
A New Android malware dubbed Xenomorph, served through Google Play Store has infected more than 50,000 Android devices to steal banking information.
Still in early development stage, Xenomorph is targeting users of dozens of financial institutions in Spain, Portugal, Italy, and Belgium.
Researchers at fraud and cybercrime prevention company ThreatFabric analyzing Xenomorph found code that is similar to Alien banking trojan. This suggests that the two threats are somehow connected: either Xenomorph is Alien’s successor or a developer has been working on both of them.
Banking trojans like Xenomorph aim to steal sensitive financial information, take over accounts, perform unauthorized transactions, and operators then sell the stolen data to interested buyers.
Sneaking into the Play Store
The Xenomorph malware entered the Google Play Store via generic performance-boosting applications such as the “Fast Cleaner”, which counts 50,000 installations.
Such utilities are a classic lure used by banking trojans, Alien included, because there’s always an interest in tools that promise to improve the performance of Android devices.
To evade rejection during the application review from the Play Store, Fast Cleaner is fetching the payload after installation, so the app is clean at submission time.
ThreatFabric recognized the application as a member of the “Gymdrop” dropper family, first discovered in November 2021, and observed pushing payloads that pose as Google Play, Chrome, or Bitcoin management apps.
Xenomorph capabilities
Xenomorph’s functionality is not full-blown at this point, as the trojan is under heavy development. However, it still represents a significant threat as it can fulfill its info-stealing purpose and it targets no less than 56 different European banks.
For example, the malware can intercept notifications, log SMS, and use injections to perform overlay attacks, so it can already snatch credentials and one-time passwords used to protect banking accounts.
After its installation, the first action taken by the app is to send back a list of the installed packages on the infected device to load the suitable overlays.
To achieve the above, the malware requests the granting of Accessibility Service permissions upon installation, and then abuses the privileges to grant itself additional permissions as needed.
Examples of commands present in the code but not yet implemented refer to keylogging functions and behavioral data collection.
Its Accessibility Engine is very detailed, and is designed with a modular approach in mind. It contains modules for each specific action required by the bot, and can be easily extended to support more functionalities. It would be unsurprising to see this bot sport semi-ATS capabilities in the very near future.
All in all, the malware may add next-level capabilities at any time, as only minor code implementations and modifications are required to activate extensive data siphoning functions.
ThreatFabric assesses that Xenomorph is not a strong threat at the moment due to its “under development” status. In time, though, it could reach its full potential, “comparable to other modern Android Banking trojans.”
To steer clear from Android malware that lurks in the Play Store, users should avoid installing apps that carry promises that are too good to be true. Checking other users’ reviews can sometimes help avoid malicious apps.
You may also enjoy reading, Q4/21: Sees More DDoS Attacks Than Ever Before
Stay informed of the latest Cybersecurity trends, threats and developments. Sign up for RiSec Weekly Cybersecurity Newsletter Today
Remember, CyberSecurity Starts With You!
- Globally, 30,000 websites are hacked daily.
- 64% of companies worldwide have experienced at least one form of a cyber attack.
- There were 20M breached records in March 2021.
- In 2020, ransomware cases grew by 150%.
- Email is responsible for around 94% of all malware.
- Every 39 seconds, there is a new attack somewhere on the web.
- An average of around 24,000 malicious mobile apps are blocked daily on the internet.