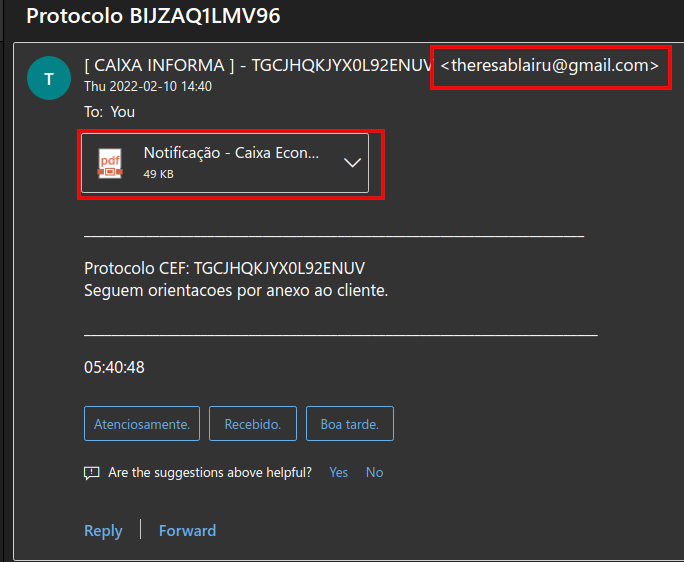
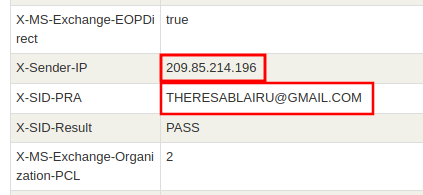
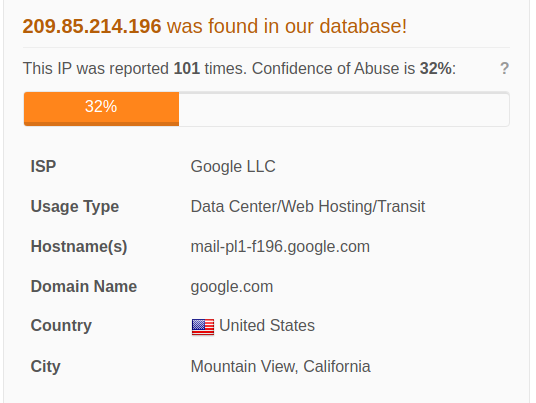
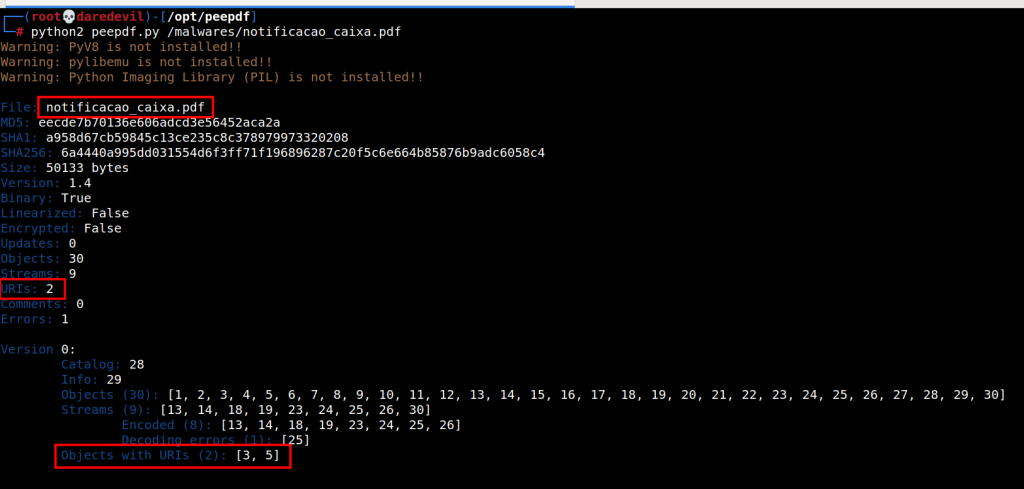
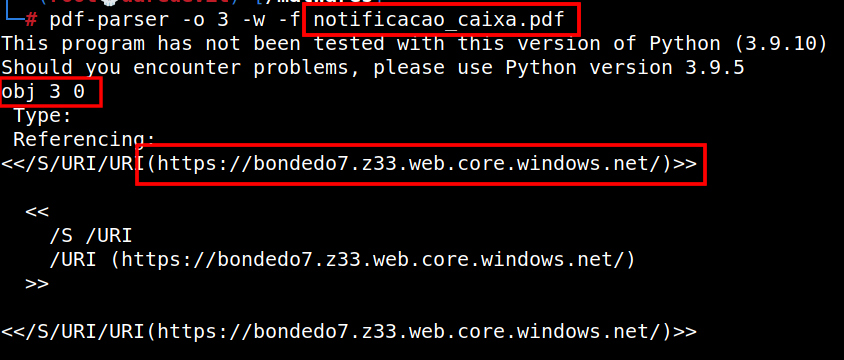
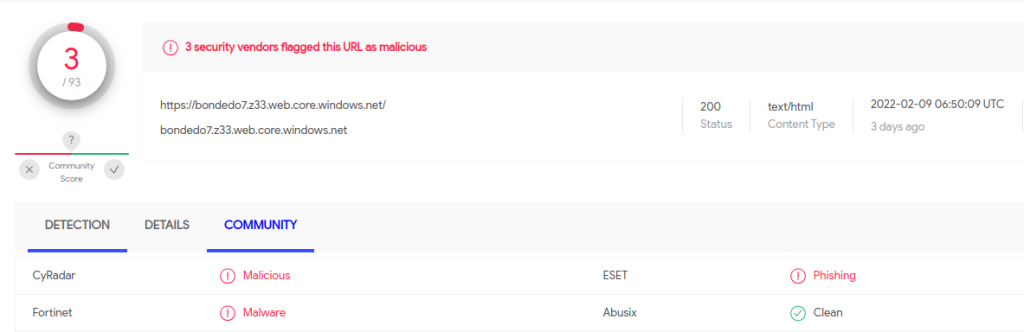
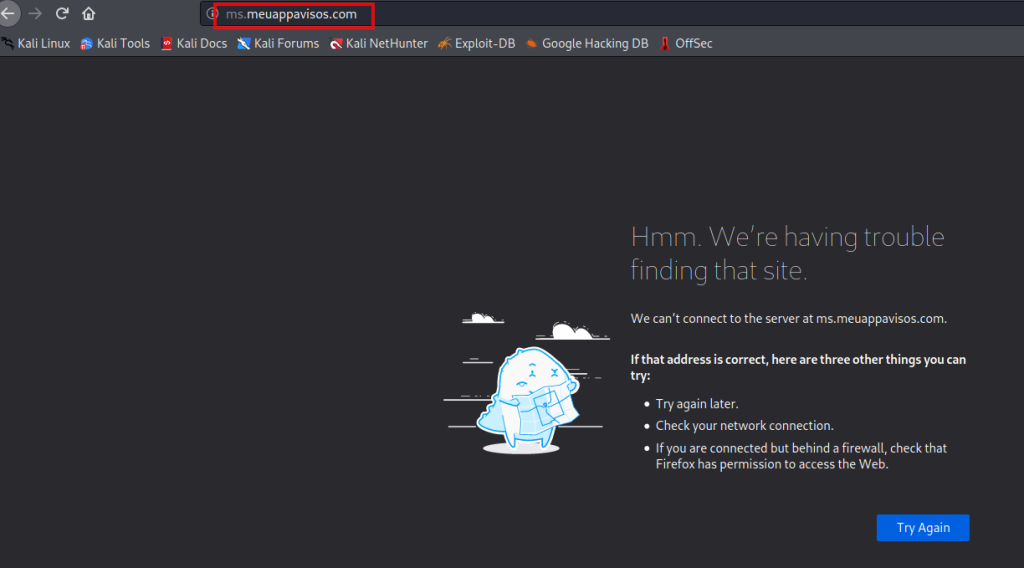
Websites for several banks and government agencies in Ukraine — including the Ministry of Defense, Ministry of Internal Affairs and the Armed Forces of Ukraine — were facing disruptions Tuesday, according to multiple sources.
Ukraine’s Center for Strategic Communications and Information Security posted a message to Facebook late morning U.S. time saying the banks and the government were hit by a “massive” distributed denial-of-service (DDoS) cyberattack.
The Ministry of Defense tweeted that it had “probably” been targeted with DDoS, and that it was communicating via Facebook and Twitter. The Ukrainian State Service of Special Communication and Information Protection called it a “powerful DDOS attack on a number of information resources,” and said experts were “taking all necessary measures to resist and localize the cyberattack.”
None of the reports attributed the DDoS attacks to a specific source. The website disruptions come as tensions in the region continue to ratchet up, with the Russian government potentially on the verge of military escalation against Ukraine.
Local news reported that users were having problems with online banking earlier in the day. One of the banks in question, Privat, is one of the largest in Ukraine, and users were having issues with the bank’s app, the government agency reported in its Facebook post. Oschad, another bank hit with attacks, also had services disrupted. Both banks are state owned. Customers for one of the state-owned banks received text messages falsely claiming that ATMs were down, the Ukrainian Cyberpolice reported Tuesday. The messages “are not phishing, but are part of an information attack and do not correspond to reality,” the agency said.
The Ministry of Defense’s website remained inaccessible midday Tuesday, displaying a message in Russian that read: “The site is under technical maintenance.” The Armed Forces of Ukraine site was also inaccessible.
DDoS attacks typically involve flooding a website with countless bogus requests until it goes down.
“Though we’ve anticipated disruptive Russian attacks against Ukraine, we’ve seen no evidence of responsibility at this time,” said John Hultquist, the vice president of threat intelligence at cybersecurity firm Mandiant. “Denial of service attacks are notoriously difficult to attribute.”
News about the potential conflict on the ground continues to revolve around possible diplomatic resolution. The Russian government had “signaled a willingness to continue talks to resolve the crisis,” and some of its troops were returning to base, the Washington Post reported earlier in the day.
Dmytro Kuleba, Ukraine’s Minister of Foreign Affairs, tweeted Tuesday morning that skepticism regarding drawdowns was warranted: “We in Ukraine have a rule: we don’t believe what we hear, we believe what we see,” he wrote. “If a real withdrawal follows these statements, we will believe in the beginning of a real de-escalation.”
The U.S. Embassy in Kyiv began moving its operations 340 miles away to Lviv on Monday, while destroying some of the IT equipment it left behind, reports said.
You may also enjoy reading, CVEs You May Have Missed While Log4J Stole The Headlines
Stay informed of the latest Cybersecurity trends, threats and developments. Sign up for RiSec Weekly Cybersecurity Newsletter Today
Remember, CyberSecurity Starts With You!
- Globally, 30,000 websites are hacked daily.
- 64% of companies worldwide have experienced at least one form of a cyber attack.
- There were 20M breached records in March 2021.
- In 2020, ransomware cases grew by 150%.
- Email is responsible for around 94% of all malware.
- Every 39 seconds, there is a new attack somewhere on the web.
- An average of around 24,000 malicious mobile apps are blocked daily on the internet.