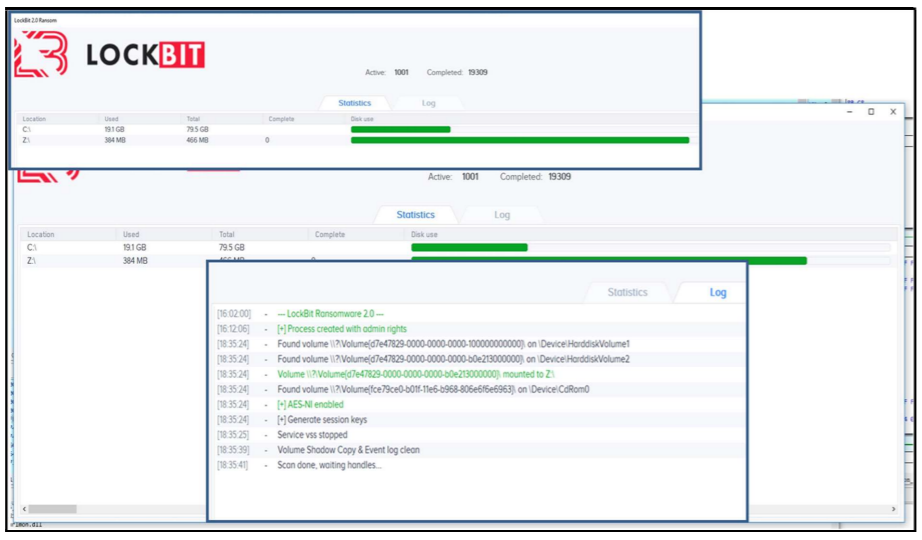
As Russia continues to amass troops at the border, resistance groups have seen a surge in crypto donations.
CRYPTOCURRENCY MAY NEVER have fulfilled its promise as the quotidian currency for buying a cup of coffee. But it’s proven to be a powerful, regulation-resistant means of sending large amounts of money anywhere in the world. That now includes war zones—or more specifically, Ukraine, a country whose long-burning, limited war with Russia and pro-Russian separatists may be about to rapidly expand.
Cryptocurrency payments to military and hacktivist groups in Ukraine aimed at countering Russian aggression against the country spiked sharply in the second half of 2021, according to cryptocurrency tracing and blockchain analysis firm Elliptic. Crowdfunded payments to those organizations in bitcoin, litecoin, ether, and other cryptocurrencies the company tracks reached a total value of around $550,000 last year, compared with just $6,000 or so in 2020 and less still in previous years, even at the height of Russia’s 2014 invasion of the country.
That half a million dollars is no doubt just a small fraction of the total funds Ukrainian defense and hacktivism groups have raised by more traditional means amid Russia’s recent escalations, says Tom Robinson, Elliptic’s founder. But the sudden rise of cryptocurrency within these global donations demonstrates how borderless, often unregulated crypto payments could fund organizations engaged in future conflicts. “Crypto is censorship-resistant, so there’s no chance they’re going to get their funds seized or their account shut down, like might happen with PayPal, and it’s also more amenable to cross-border donations,” says Robinson. “It’s proved itself to be a robust way to fund wars.”
One Ukrainian group called Come Back Alive, for instance, has raised $200,000 for Ukrainian troops in just the second half of 2021, according to Elliptic. The group originally solicited donations for military equipment like bulletproof vests, but it has since expanded into funding the purchase of reconnaissance and targeting systems. A more controversial group called the Myrotvorets (Ukrainian for “Peacemaker”) Center has publicly named and shamed alleged supporters of Russia or pro-Russian separatists in Ukraine—at least two of whom were subsequently assassinated. Myrotvorets has raised $268,000 in cryptocurrency to date, Elliptic says, of which $237,000 came just in the second half of last year.
Pro-Ukrainian hacktivists, too, have increasingly funded their digital resistance through cryptocurrency. Elliptic traced around $100,000 worth of crypto donations to a hacker group called the Ukrainian Cyber Alliance, which has been responsible for numerous hack-and-leak and web defacement operations targeting Russians and Russian government agencies. Cyber Partisans, a Belarusian hacktivist group that gained global attention by launching a politically motivated ransomware attack on Belarus’ rail system, has also raised around $84,000 in cryptocurrency. (Elliptic included that number in its $550,000 total, despite the group self-identifying as Belarusian rather than Ukrainian, due to the hackers’ support for Ukraine and demand that Belarusian Railways cease transporting Russian troops in preparation for any invasion of Ukraine.)
Payments to Ukrainian war-effort organizations or even pro-Ukrainian hacktivists aren’t necessarily illegal or in violation of any sanctions. But the Myrotvorets Center said that at least one of its PayPal accounts, intended to fund a facial recognition program, was seized due to the complaints about “terrorists and Russians.”
Cryptocurrency exchanges that convert donated bitcoin into dollars or Ukrainian hryvna, on the other hand, are often far less closely regulated. And Elliptic’s Robinson argues that cryptocurrency offers advantages to donors, who may not want their banking records to show that they sent money to organizations that might be perceived as paramilitary groups. “If I were going to make a donation of this kind, I’d be much better off using crypto than a bank transfer,” Robinson says.
The disadvantage of cryptocurrency, of course, is that in some respects it’s even less private than the traditional banking system—as Elliptic’s own ability to track the Ukrainian groups’ donations through blockchain analysis shows. Elliptic competitor Chainalysis, for instance, identified a software developer in France who donated $500,000 to many participants in the January 6 riot at the US Capitol. (Robinson says that Elliptic didn’t attempt to identify individual donors to the Ukrainian groups, though it might be possible to do so with “some legwork,” especially if a government agency demanded identifying information from cryptocurrency exchanges.)
Nor are international cryptocurrency donations intended for military operations always immune to seizure. In another group of cases announced in August of 2020, the US Justice Department traced and confiscated about half a million dollars’ worth of cryptocurrency donations from a collection of designated terrorist organizations, including the militant wing of the Palestinian group Hamas known as the al-Qassam Brigades.
You may also enjoy reading, The largest DDoS to date, Microsoft mitigates a 3.47 Tbps DDoS attack
Stay informed of the latest Cybersecurity trends, threats and developments. Sign up for RiSec Weekly Cybersecurity Newsletter Today
Remember, CyberSecurity Starts With You!
- Globally, 30,000 websites are hacked daily.
- 64% of companies worldwide have experienced at least one form of a cyber attack.
- There were 20M breached records in March 2021.
- In 2020, ransomware cases grew by 150%.
- Email is responsible for around 94% of all malware.
- Every 39 seconds, there is a new attack somewhere on the web.
- An average of around 24,000 malicious mobile apps are blocked daily on the internet.