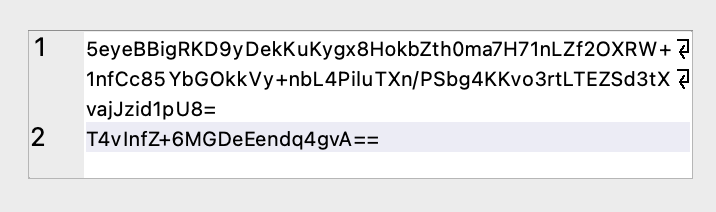
Russian cybercriminals known as the Turla group have repurposed an old malware infrastructure to deploy new backdoors and infect victims’ systems. The group, which has been active since at least 2007, is known for its sophisticated campaigns targeting government and diplomatic organizations, as well as private sector companies.
In this recent campaign, the hackers were able to compromise the infrastructure of an older malware strain, allowing them to use it to launch new attacks and evade detection. The Turla group is known for its ability to leverage a wide range of tools and techniques to carry out its operations, and this latest campaign underscores the group’s continued evolution and adaptability.
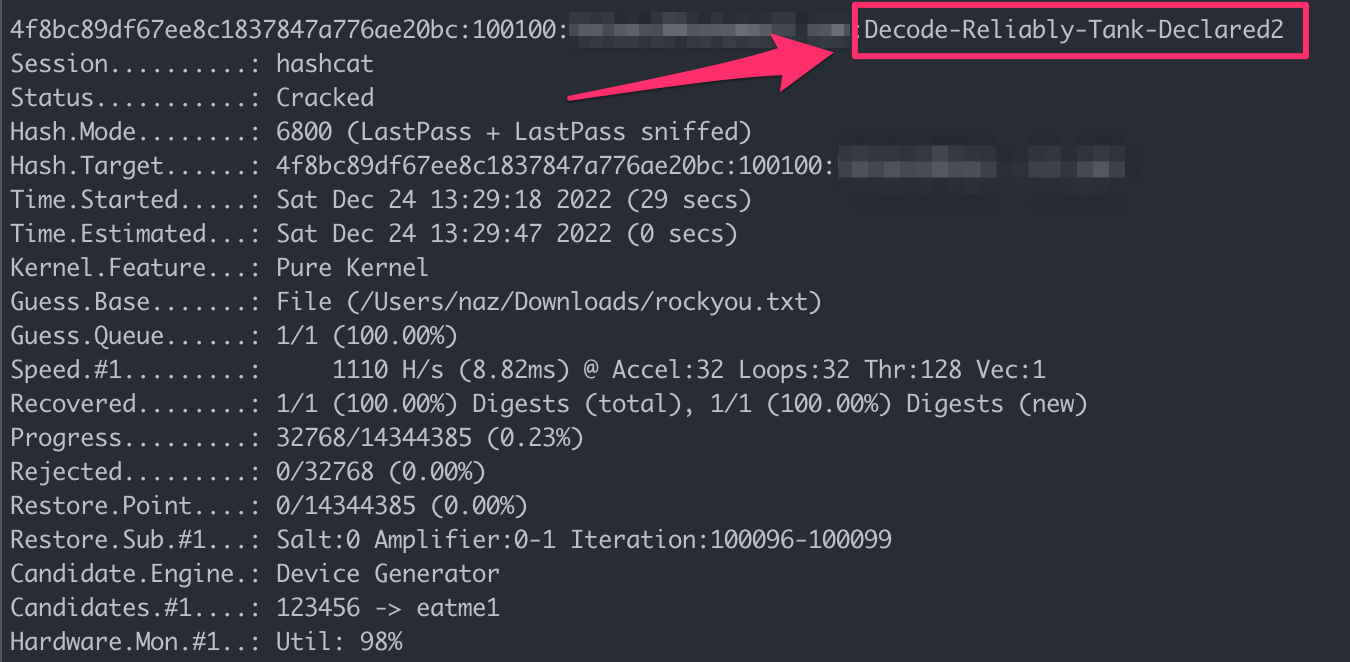
The servers were taken over by a variation of a common virus dubbed ANDROMEDA (also known as Gamarue), according to Google-owned Mandiant, which is monitoring the operation under the uncategorized cluster identifier UNC4210. This malware was posted to VirusTotal in 2013.
“UNC4210 re-registered at least three expired ANDROMEDA command-and-control (C2) domains and began profiling victims to selectively deploy KOPILUWAK and QUIETCANARY in September 2022,” Mandiant researchers said in an analysis published last week.
Turla, also known by the names Iron Hunter, Krypton, Uroburos, Venomous Bear, and Waterbug, is an elite nation-state outfit that primarily targets government, diplomatic, and military organizations using a large set of custom malware.
Since the onset of Russia’s military invasion of Ukraine in February 2022, the adversarial collective has been linked to a string of credential phishing and reconnaissance efforts aimed at entities located in the country.
To allegedly “assist” pro-Ukrainian hacktivists in launching distributed denial-of-service (DDoS) assaults against Russian websites, Turla allegedly developed a malicious Android app in July 2022, according to Google’s Threat Analysis Group (TAG).
The most recent discovery from Mandiant demonstrates how Turla has been covertly appropriating prior infections as a malware distribution strategy, in addition to profiting on ANDROMEDA’s ability to spread via infected USB keys.
“USB spreading malware continues to be a useful vector to gain initial access into organizations,” the threat intelligence firm said.
In the incident analyzed by Mandiant, an infected USB stick is said to have been inserted at an unnamed Ukrainian organization in December 2021, ultimately leading to the deployment of a legacy ANDROMEDA artifact on the host upon launching a malicious link (.LNK) file masquerading as a folder within the USB drive.
The threat actor then repurposed one of the dormant domains that were part of ANDROMEDA’s defunct C2 infrastructure – which it re-registered in January 2022 – to profile the victim by delivering the first-stage KOPILUWAK dropper, a JavaScript-based network reconnaissance utility.
Two days later, on September 8, 2022, the attack proceeded to the final phase with the execution of a .NET-based implant dubbed QUIETCANARY (aka Tunnus), resulting in the exfiltration of files created after January 1, 2021.
The tradecraft employed by Turla dovetails with prior reports of the group’s extensive victim profiling efforts coinciding with the Russo-Ukrainian war, potentially helping it tailor its follow-on exploitation efforts to harvest the information of interest to Russia.
It’s also one of the rare instances where a hacking unit has been identified targeting victims of a different malware campaign to meet its own strategic goals, while also obscuring its role.
“As older ANDROMEDA malware continues to spread from compromised USB devices, these re-registered domains pose a risk as new threat actors can take control and deliver new malware to victims,” the researchers said.
“This novel technique of claiming expired domains used by widely distributed, financially motivated malware can enable follow-on compromises at a wide array of entities. Further, older malware and infrastructure may be more likely to be overlooked by defenders triaging a wide variety of alerts.”
COLDRIVER Targets U.S. Nuclear Research Labs#
The findings also come as Reuters reported that another Russian state-sponsored threat group codenamed COLDRIVER (aka Callisto or SEABORGIUM) targeted three nuclear research labs in the U.S. in early 2022.
To that end, the digital assaults entailed creating fake login pages for Brookhaven, Argonne, and Lawrence Livermore National Laboratories in an attempt to trick nuclear scientists into revealing their passwords.
The tactics are consistent with known COLDRIVER activity, which recently was unmasked spoofing the login pages of defense and intelligence consulting companies as well as NGOs, think tanks, and higher education entities in the U.K. and the U.S.
Suggest an edit to this article
Check out our new Discord Cyber Awareness Server. Stay informed with CVE Alerts, Cybersecurity News & More!
Remember, CyberSecurity Starts With You!
- Globally, 30,000 websites are hacked daily.
- 64% of companies worldwide have experienced at least one form of a cyber attack.
- There were 20M breached records in March 2021.
- In 2020, ransomware cases grew by 150%.
- Email is responsible for around 94% of all malware.
- Every 39 seconds, there is a new attack somewhere on the web.
- An average of around 24,000 malicious mobile apps are blocked daily on the internet.