A report on the underground economy finds that malicious actors are offering cloud-based troves of stolen data, accessible with handy tools to slice and dice what’s on offer.
Cybercriminals are embracing cloud-based services and technologies in order to accelerate their attacks on organizations and better monetize their wares, researchers have found. This is largely driven by cybercriminals who sell access to what they call “clouds of logs,” which are caches of stolen credentials and other data hosted in the cloud.
The cloud-based approach makes the information more easily available to interested buyers, who then turn around and use the data to conduct secondary attacks, according to Trend Micro. Malicious actors are offering “cloud-based tools [to buyers] for analyzing and extracting the data that they need to conduct [these] further malicious activities,” explained the firm in a Monday posting, which characterized the development as a relatively new approach.
The move to the cloud for cybercriminals has the same main benefit as it does for legitimate organizations: Speed. Trend Micro said that the time between an initial data heist to that stolen information being used against an enterprise has decreased from weeks to days or even hours when the cloud approach is taken.
“With the introduction of cloud-based services and technologies, criminals are equipped to steal, purchase and use data to conduct their attacks much faster when targeting organizations,” researchers said, using the analogy of the time it takes someone to buy their tools at a garage sale versus buying them from an online shopping site.
And with faster transactions in play, “organizations would not be able to anticipate the arrival and speedy execution of such attacks — ones enabled by stolen data and orchestrated by criminals with only a short amount of time, leaving them with less time to detect and respond.”
A Big Data Problem
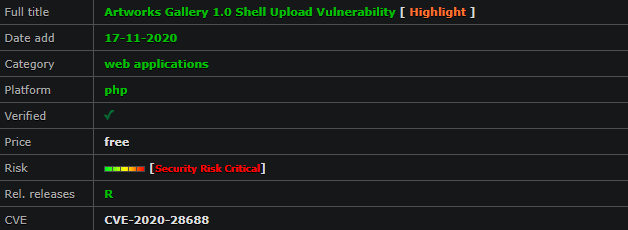
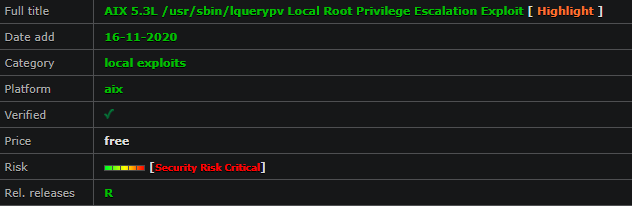
Malicious actors are turning to the cloud in order to work more effectively with the sheer volume of data on offer in underground forums, researchers said. By Trend Micro’s estimation, the caches represent multiple terabytes-worth of data.
“In recent years, the theft of user credentials has been on the rise, with attackers collecting massive amounts of credentials and associated email addresses or domain names,” researchers explained. “[Other data stolen] often includes recorded keystrokes, authentication credentials to online portals, online banks, authenticated session attributes, personally identifiable information (PII), scans of documents, tax reports, invoices, bank account payment details (for example, credit cards), and more.”
Exacerbating the situation is the fact that data exfiltration has become de rigueur for almost any type of attack, including ransomware, botnets, keyloggers, exploit kits and other malicious components.
“In addition to what was previously mentioned, this collected information might contain browsing history, cookies, keystrokes, user credentials, authentication tokens, information about the victim environment that can be used to evade anti-fraud systems, and more,” researchers said.
All of this means that cybercriminals have a Big Data problem – again, just like legitimate organizations. It’s hard to exploit the full potential of such a colossal amount of data without tools for slicing and dicing it.
This has paved the way for a pay-for-access business model that allows cybercriminals to better monetize their ill-gotten goods while enabling other attackers to easily identify the data that they will need from sellers’ clouds of logs for their attacks.
Pay-for-Access in the Cloud Economy
Customers pay to access the “clouds of logs” using helpful cloud tools at varying price ranges, Trend Micro found.
Packages that only allow limited access and downloads are in the hundred-dollar range. Monthly subscription rates are also offered, with some cybercriminals pricing them within the $300 to $1,000 per-month range.
“[One actor] claims to update their dataset with new stolen accounts on a weekly basis,” according to the firm. “The service offers a premium subscription for $300 for the first four customers, while further access is priced at $1,000.”
In another instance, an advertisement of a service guarantees updates of new batches of data ranging from 20,000 to 30,000 logs every one to two weeks. A monthly subscription costs $1,000, while a semiannual subscription costs $5,000.
The data can be separated by country or region, data type, whether or not the logs have been used before in other campaigns, victim organization name or sector, and other parameters.
“Criminals only need to search for the data that they need in order to find an opportunity to commit a crime faster; after all, they won’t have to do the task of obtaining data by themselves anymore,” the firm explained.
Criminals who buy access to these datasets also vary in their specializations, according to Trend Micro.
“Some of these criminals primarily focus on carding activities, while others specialize in attacking financial institutions and seek banking credentials,” according to the report. “Credentials for accessing cloud platform portals are also sold to those criminals who specialize in selling bulletproof-dedicated services. Such credentials could be used to spawn instances of virtual machines that are then sold in underground markets.”
As discussed earlier, many sellers also limit the number of people who can access and buy logs. They also implement data watermarking and other tracking methods to enforce their service-level agreements (SLA).
“Among these restrictions are fixed quotes on the total number of accessed objects per day, a restriction on the number of files permitted for download, or the implementation of traffic-shaping policies,” according to Trend Micro. “Other platforms also restrict access to the cloud to one device per account. Some also require private VPN credentials to initiate access to the service.”
Future is Cloudy
With the growing business of selling access to clouds of logs, various monetization schemes could arise in the future, according to Trend Micro.
“For instance, cybercriminals could look for records of authenticated user sessions to cloud portals,” the firm explained. “If a malicious actor hijacks an active console session from a cloud service provider, they could have full control of the victim’s cloud resources. This could mean gaining access to existing cloud systems and storage. The actors could then sniff valuable data from these resources, which they could in turn exfiltrate and sell in the underground.”
Researchers also foresee malicious actors developing tools powered by machine learning (ML) to speed up data extraction and analysis processes.
“Although we have only seen tools with limited capacities as of writing, we believe that the development of ML-powered tools — ones that can scale much larger datasets at a faster rate — is the next logical step for criminals as the market matures,” the report concluded
Bookmark Please login to bookmarkClose