The past three months have been a particularly challenging time for security teams. 2021 rounded off in the most spectacular fashion—if you can call it that—with the discovery of the Log4Shell vulnerability leaving security teams scrambling to identify and fix systems before threat actors could exploit. We’ve written a considerable amount on the issues surrounding Log4Shell, with our previous blogs covering the initial scope following the disclosure, an update on a second vulnerability related to Log4j, and the aftermath of threat actors targeting the bug.
As with any period of upheaval and turmoil, other issues will be missed or otherwise kicked down the priority list. While Log4j is incredibly serious and should be patched with the highest priority, there are several nasty vulnerabilities that can also cause significant disruption in 2022. Don’t panic, though. We’ve got you covered by highlighting these vulnerabilities through the prism of our new vulnerability intelligence solution that’s available in SearchLight. If you haven’t had a chance to glance through this new feature, please take a look at our blog here and our solutions guide, detailing this fantastic product in great detail.
WHY IS VULNERABILITY INTELLIGENCE SO IMPORTANT?
The best place to start this blog is to detail the importance of vulnerability intelligence, which is emerging as one of the key threat intelligence use cases. Vulnerability intelligence allows organizations to reduce the noise of the thousands of active vulnerabilities in circulation and take a risk-based approach in prioritizing the vulnerabilities that matter the most. A risk-based approach is determined by looking at the current threat landscape, which can provide intelligence on the risk posed by each vulnerability. Factors determining this risk can include its exploitability, the scale of devices the vulnerability affects, and interest from malicious actors. Vulnerability intelligence, in the end, exists to provide actionable insights for vulnerability management, allowing organizations to move away from an obsolete approach of attempting to fix everything.
WHICH VULNERABILITIES WERE EXPLOITED IN Q4 2021?
Digital Shadows identified 260 vulnerabilities through referenced intelligence as having been exploited in Q4 2021. Referenced intel can be defined as entries collected by crawlers parsing a range of sources (e.g., Twitter, Git) before assigning tag associations in Searchlight, depending on their content. A breakdown of the 260 vulnerabilities by VulDb 3.0 CVSS score can be seen in the graphic below, with the majority of the exploited vulnerabilities from this period being within the range of CVSS score of 7-8 (high). This emphasizes that while critical vulnerabilities of course need to be addressed in a timely manner, the pinch point for threat actor exploitation is often in the middle range, targeting vulnerabilities that potentially may have been overlooked by security teams; this does however likely reflect the typical bell curve of CVSS scores. Most fall within the range of around 5-7.
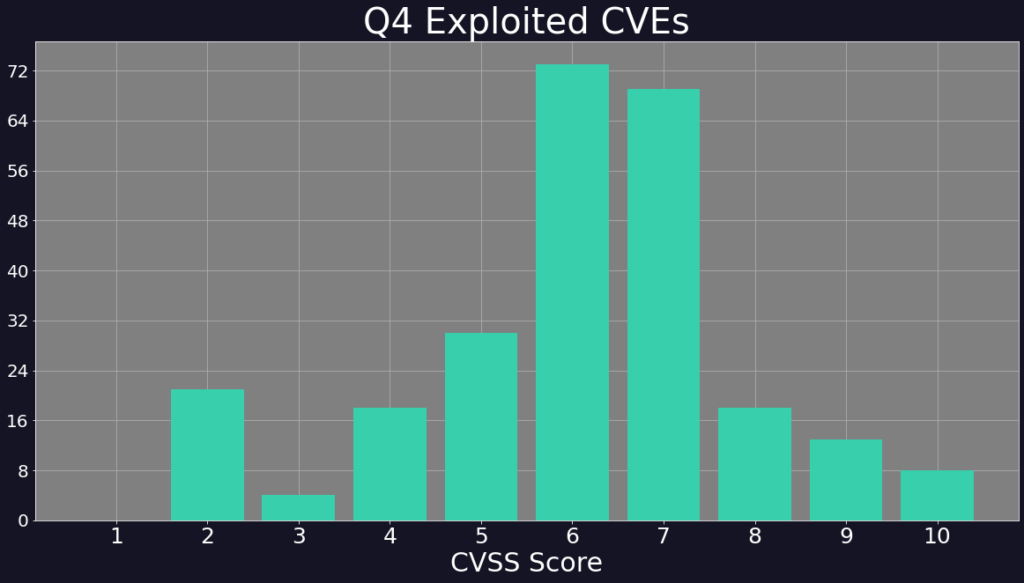
In an ideal world, all of these vulnerabilities should be patched by security teams as soon as is feasible. If they’re being exploited in the wild, that means that threat actors have developed a method of using the vulnerabilities to solicit various malicious campaigns. If you have exposure to these, it’s only a matter of time before you see misuse on your network related to these bugs.
However, of these 260 associated with active exploitation, which is the priority? After all, taking a risk-based approach will always be the best way to remediate software bugs; fixing everything at once isn’t an option, and not all vulnerabilities present the same risk. In order to fine-tune our investigation, we used our new vulnerability intelligence filter within Searchlight to search for vulnerabilities that were exploited in the wild, known to be embedded in pentest tools, did not require user privileges or user interaction, were remotely exploitable, and had a CVSS score of 7.5 or higher. These tags represent just a fraction of the available filtering options; you can easily tune searches based on your specific organizational requirements.
THE VULNERABILITIES YOU MAY HAVE MISSED OVER LOG4J
In addition to Log4Shell, also included in this smaller pool of 6 vulnerabilities were the ProxyLogon and ProxyShell vulnerabilities that we’ve discussed in great depth before —and which we’ll touch upon later—and three other vulnerabilities that you might not have heard about or otherwise missed during this frantic period.
The one that allows RCE on MSHTML (CVE-2021-40444)
We want to start on CVE-2021-40444, a critical remote code execution (RCE) vulnerability that attackers can exploit to execute any code or commands on a target machine without the owner’s knowledge. This vulnerability impacts MSHTML, a core component in Windows, allowing the OS to render web pages. Although it’s most commonly associated with Internet Explorer, this component is also used in other software, including Skype, Microsoft Outlook, Visual Studio, and others. Spotting the potential impact of this vulnerability, Microsoft swiftly moved to issue a mitigation with an update following September’s Patch Tuesday update.
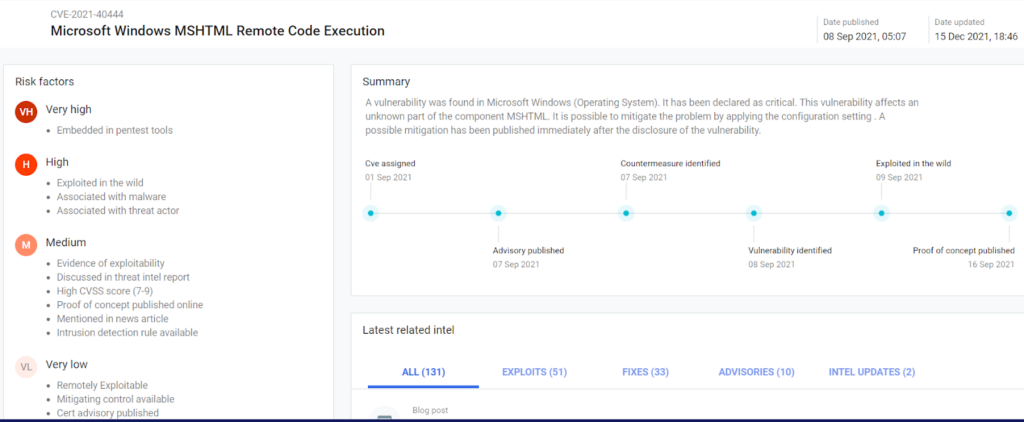
The bug has garnered significant attention from threat actors since August 2021. Microsoft first identified that threat actors were exploiting CVE-2021-40444 through specially crafted Microsoft Office documents to run malicious code, many of which were used to implant Cobalt Strike beacons onto networks; Cobalt Strike almost always is followed by further exploitation, with the commonly used penetration testing framework used by a diverse range of threat actors and groups. The observed attack vector relied on a malicious ActiveX control that could be loaded by the browser rendering engine using a malicious Office document. These were reportedly delivered via emails impersonating contracts and legal agreements, with the documents hosted on file-sharing sites. The malicious document then retrieves a cabinet (CAB) file that remotely loads the Cobalt Strike beacon loader when executed. An attack chain for this vulnerability can be seen in the graphic below, with Microsoft naming the associated threat actor “DEV-0413”.
Other exploitation attempts in December 2021 have used a CAB-less version of the attack by using a different compressed file format, a RAR archive. The attack resulted in the distribution of the FormBook malware, a common infostealer first identified in 2016. The attack reportedly can evade the original patch issued by Microsoft, once again highlighting the persistence and agility of threat actors in finding new ways to target vulnerabilities, even after they have been fixed.
One key feature of the exploitation of CVE-2021-40444 that makes this vulnerability so dangerous is a key feature of Microsoft Office in ensuring protection from malicious external documents can easily be bypassed. If an Office document has been downloaded from the Internet or sent as an email attachment, it should contain a bit of extra information in its alternate data stream (ADS). In the case of a downloaded document, it should contain the ‘mark of the web’ (MOTW), which leads to Microsoft Office opening that document in Protected View. Protected View has been confirmed to prevent the automatic execution of this vulnerability.
Humans are, however, naturally curious, and many will ignore these warnings and click to ignore protected view, thus allowing the malicious document to exploit the vulnerability. If an Office document is delivered via a ZIP file—and the Office document is extracted locally onto the disk—the Zone.Identifier may not be present and the exploit will run once the document is opened. The exploit has also been observed to run when a document is previewed in Windows Explorer. It seems pretty obvious advice, but be aware of what you are enabling and always treat documents received from unknown or unverified sources with the highest levels of suspicion.
The one granting GOD-like privileges (CVE-2021-38647 / CVE-2021-38648)
Another series of vulnerabilities that were identified through our triage of exploited vulnerabilities in Q4 is CVE-2021-38647, a RCE vulnerability affecting the Open Management Instrumentation (OMI). This RCE coincides with three other high severity vulnerabilities, CVE-2021-38648, CVE-2021-38645, and CVE-2021-38649, which together have been appropriately named OMIGOD. OMI is an open-source Web-Based Enterprise Management (WBEM) implementation for managing Linux and UNIX systems. Several Azure Virtual Machine (VM) management extensions use OMI to orchestrate configuration management and log collection on Linux VMs. The originating researchers who discovered this vulnerability have compared OMI to Window Management Instrumentation (WMI) that is used in Linux/Unix systems.
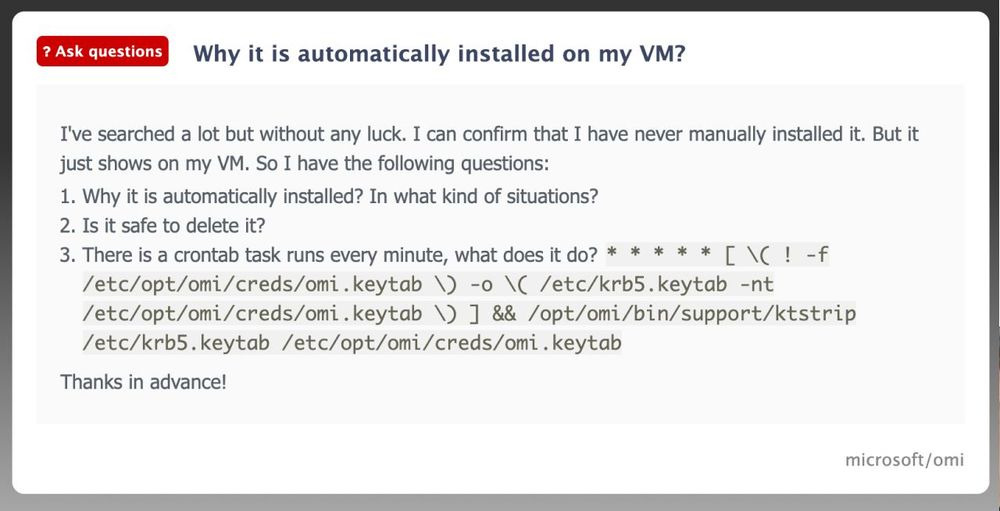
OMI is installed in a vast repertoire of Microsoft Azure products, including Azure Automation, Azure Automatic Update and Azure Log Analytics. This factor is also exacerbated since OMI is reportedly installed without the customer’s knowledge. OMI is automatically installed on user’s devices during setup and runs with the highest privileges. As demonstrated by the discussion board query below, many users have been frustrated with the lack of documentation detailing what OMI is and why it’s required.
The originating researchers clarified that OMIGOD allowed external or lower privileged users to execute code on targeted machines or to escalate privileges. Microsoft fixed the bug in September 2021; however, reportedly will still issue vulnerable versions of the OMI agents for new Linux VMs created in Azure. Users looking to update will also be forced to manually update their susceptible Azure systems, as Microsoft has no mechanism available to auto-update vulnerable agents on all impacted Azure Linux machines. Threats known to be targeting OMIGOD include the Mirai botnet, which reportedly closed the 5896 OMI SSL port after gaining persistence on a susceptible device. Mirai’s operators likely conducted this activity to stop the exploit for OMIGOD being open to other threats, which highlights how easy to exploit the bug is.
So just to summarise; OMIGOD is highly exploitable and can provide attackers with significant opportunities, will likely fly under the radar due to the lack of awareness of OMI, and ultimately is extremely difficult for admins to patch. Combining all these factors makes OMIGOD a serious risk that we don’t believe has received the necessary attention it deserves.
The one exploited by China-linked “Iron Husky” (CVE-2021-40449)
Another vulnerability that needs to be discussed is CVE-2021-40449, a privilege escalation vulnerability affecting several versions of Windows Server and client systems and may be used to escalate privileges on an already compromised system. This bug was initially divulged back to the security community in October, with the exploitation of the vulnerability occurring almost immediately following its disclosure. A timeline of the vulnerability lifecycle can be seen on Searchlight portal profile in the graphic below.
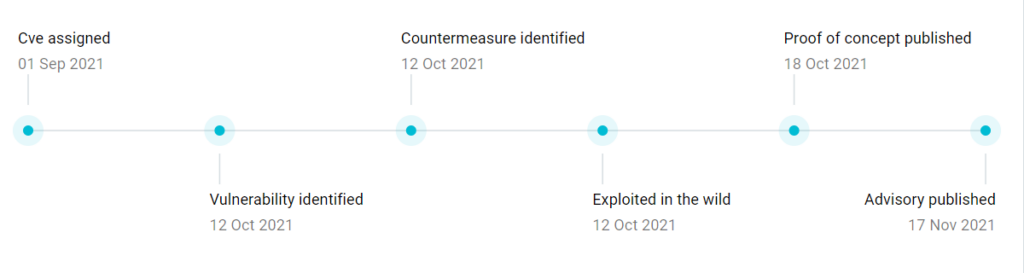
The bug, which has been incorporated on threat actor pen-testing tools, has been targeted by a China-linked advanced persistent threat (APT) group named “IronHusky,” which has conducted intrusions since 2016. IronHusky reportedly targeted the vulnerability in Win32k.sys, a legitimate file process developed by Microsoft and part of the Graphics Device Interface (GDI). Attackers could use the vulnerability to install a remote access trojan (RAT) named “MysterySnail” which can execute Windows shell commands, gather information about the disks and folders, delete, read and upload files, kill processes, and more. Analysis of MysterySnail allowed researchers to attribute to IronHusky, who has previously conducted a range of cyber espionage operations, likely prioritized geopolitical reasons.
WHICH VULNERABILITIES WERE ASSOCIATED WITH MALWARE OR RANSOMWARE ACTORS?
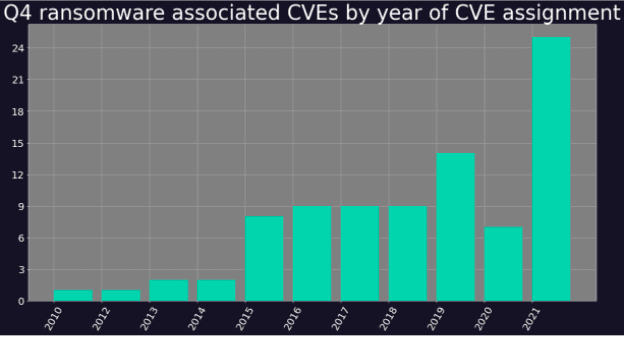
Digital Shadows identified 87 vulnerabilities associated with ransomware activity which received our intelligence updates from Q4 2021 (a breakdown of this data by year of CVE assignment can be seen in the graphic below). As you’d expect, a significant percentage of these vulnerabilities were disclosed in 2021, highlighting the importance for companies to remediate recent vulnerabilities before cybercriminals have a chance to exploit them. New vulnerabilities will always solicit interest for ransomware groups, and with half of all exploits emerging in the two weeks following disclosure, organizations only have a short amount of time to patch before seeing live attacks in the wild.
However, new vulnerabilities may not necessarily be the most critical to patch for an organization. Many older vulnerabilities also continue to be targeted by cybercriminal groups; What’s the reason for this? Well, many companies still operate with the “if it’s not broken, why fix it” mindset. If organizations continue to leave gaps on their networks from older vulnerabilities, threat actors will continue to exploit them. At the end of the day, most threat actors are opportunistic in nature and would rather go for the low hanging fruit rather than developing expensive and sophisticated tools to exploit the latest, shiniest CVE out there.
The inglorious “ProxyShell” ones (CVE-2021-34473, CVE-2021-34523, CVE-2021-31207)
So, where better to start discussing ransomware-associated CVEs than the ProxyShell bugs initially discovered in July 2021 to quite the fan fair. ProxyShell is the name of an exploit utilizing three chained Microsoft Exchange vulnerabilities (CVE-2021-34473, CVE-2021-34523, CVE-2021-31207) that allow unauthenticated, remote code execution on unpatched vulnerable servers. ProxyShell followed the four “Proxylogon” vulnerabilities that were identified in March 2021 (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065), and just to complicate matters further, “ProxyToken” (CVE-2021-33766).
As highlighted in our recent update blog on ransomware activity in Q4 2021, Proxyshell has been targeted by multiple ransomware groups. Of the groups targeting ProxyShell, Conti, the second most active group during this period, was perhaps most notable. Conti exploited Proxyshell as a medium to initially compromise networks. Conti followed a similar attack path to many other actors targeting Proxyshell by uploading web shells used to execute commands, download software, and further compromise the server. Once the threat actors gained complete control of the server, Conti moved to their typical routine of establishing liars of domain admins and endpoints, dumping LSASS to access other admin credentials, and spreading laterally. Persistence is also established by installing remote tools like Cobalt Strike and AnyDesk.
Conti is an enormous threat to business, which has been known to target a wide array of sectors and geographies and can turn over an attack in a rapid amount of time. If you haven’t patched for the Proxyshell vulnerabilities yet, now certainly would be a good time!
The one targeting QNAP Network Attached Storage (CVE-2021-28799)
If you’re an owner of a QNAP Network Attached Storage (NAS) device, you’ll want to tune in for this one. CVE-2021-28799 is an improper authorization vulnerability that affects QNAP NAS running HBS 3 (Hybrid Backup Sync). This bug was identified in April 2021, with exploitation beginning almost immediately. The QLocker ransomware exploited CVE-2021-28799 to access QNAP NAS devices and encrypt their files. The exploitation of this bug has since resumed in Q4 2021, with the “ech0raix” ransomware hitting susceptible QNAP devices in December 2021 and Qlocker returning to the well in January 2022. Other activity targeting QNAP NAS has been detected in late January, which was attributed to the DeadBolt ransomware.
Besides making sure devices are patched with the most recent update, QNAP has issued security advice for securing devices, which includes reducing the attack surface and several steps to harden security. Ensuring that devices are not internet facing is also a crucial step, which can remove the risk from several unsophisticated malware types like DeadBolt.
What older bugs are ransomware groups exploiting?
What about the older bugs we touched upon before? Well, why not go way back in time and start with CVE-2012-0158. This Microsoft Office bug has been in circulation in threat campaigns for many years, allowing threat actors to hijack Microsoft Word or Excel and force these programs to execute malicious code. This ancient bug was identified as within the top four vulnerabilities targeted by ransomware groups in 2020, and its use has continued into 2021. If you want an example of how organizations fail to identify and remediate old yet exploitable bugs, this is probably it.
Another older vulnerability that is also not being addressed by organizations is CVE-2019-7481, an SQL injection vulnerability affecting SonicWall Secure Remote Access (SRA) 4600 devices running firmware versions 8.x and 9.x. Targeting remote services—which heavily include VPN devices —has become a mainstay of cybercriminal and nation-state threat actors due to the increase in the use of such software brought on by the COVID-19 pandemic. Just like COVID-19, increased use of such software is here to stay.
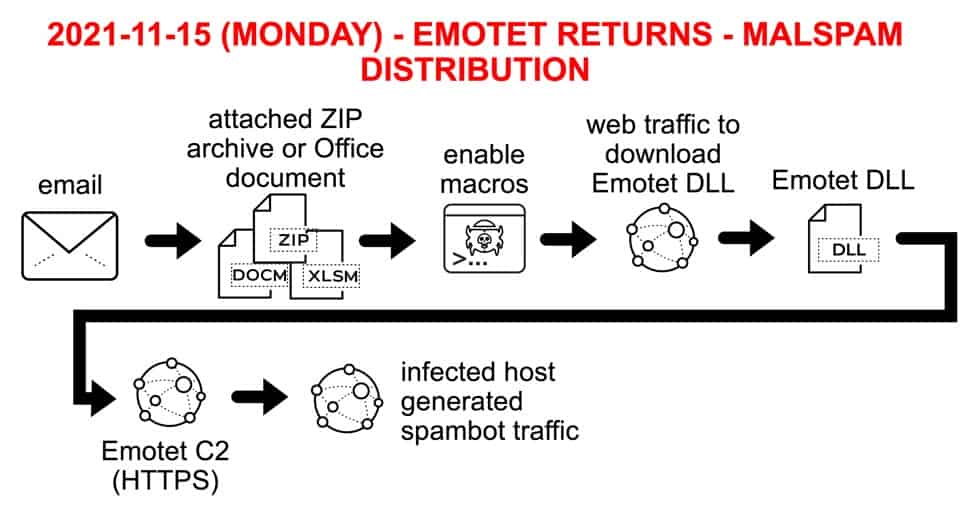
Also worth your attention is CVE-2018-12808, which affects Adobe Acrobat Reader and has been used frequently to deliver ransomware via phishing emails and malicious PDF files. The use of CVE-218-12808 has been associated with the Ryuk ransomware group and their probable successor, Conti, as a method of gaining initial access to targeted companies. In November, you probably saw that the Emotet malware returned from a 10-month hiatus after initially being taken down by a law enforcement operation in January 2021. The developers of Emotet reportedly took this decision to return following pressure being placed on them by operators of Conti. The latter is known to have significantly used Emotet to facilitate initial access to target companies. Malicious Office documents and PDFs are a key part of Emotet malspam distribution, and bugs like those affecting Adobe Acrobat will likely continue within the attack lifecycle of groups like Conti.
WHICH VULNERABILITIES WERE DISCUSSED IN CRIMINAL LOCATIONS?
Also available on Searchlight’s vulnerability intelligence portal is a filter for ‘discussed on criminal location.’ When used in conjunction with a date range for Q4 2021, 31 CVE’s were identified. This acts as a useful starting point to determine which CVEs are being targeted by threat actors, with common discussions involving exploitation methods, identification of susceptible systems, or other insights. These discussions can dramatically impact a CVE’s risk, and being aware of which CVEs are being discussed is a useful way to stay one step ahead.
Path traversal vulnerability (CVE-2021-41773)
CVE-2021-41773 is a path traversal vulnerability affecting Apache HTTP Server Project and originally identified on 29 Sep 2021, and exploited in the wild before being patched on 05 Oct 2021. This vulnerability only impacts Apache HTTP Server version 2.4.49 with the “require all denied” access control configuration disabled. Successful exploitation would give a remote attacker access to arbitrary files outside the document root on the vulnerable web server. Shodan searches in early October 2021 identified around 112,000 servers susceptible to this bug, which determines the scale of devices that attackers have to work with for this vulnerability.
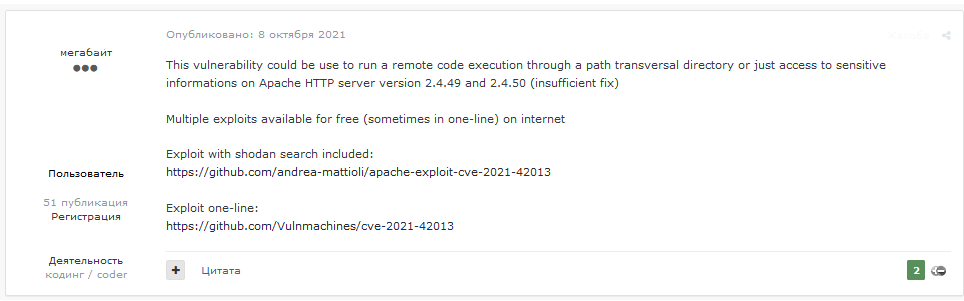
The CVE quickly generated significant interest from cybercriminal actors on various forums. One threat actor was identified on a prominent cybercriminal forum on 08 Oct 2021, sharing two links to two GitHub submissions of exploits for “Path transversal & RCE Apache server” CVE-2021-41773 and CVE-2021-42013.” The user wrote that these vulnerabilities could be used to run a remote code execution through a path transversal directory or to access sensitive information on Apache HXXP server versions 2.4.49 and 2.4.50.
Responses to this thread continued a theme of interest in targeting this specific vulnerability, with one user replying that “apache RCE exploits are always a good way to get servers”. Other threads related to this vulnerability identified methods of exploiting this bug, discussed issues with identifying the CVE using Shodan, and how certain commands could be used to illuminate susceptible servers. Apache remains the most popular web server across the globe—and as demonstrated by the recent Log4Shell bug—any exploitable CVEs affecting Apache will always generate significant threat actor interest.
File upload vulnerability (CVE-2021-22005)
Another vulnerability that generated interest from cybercriminal actors was CVE-2021-22005, a file upload vulnerability that can be used to execute commands on VMWare’s vCenter Server Appliance; vCenter is a server management solution that helps IT admins manage virtualized hosts and virtual machines in enterprise environments via a single console. Threat actors can exploit CVE-2021-22005 through vCenter Server Appliance connected over port 443 (HTTPS). The attackers would then be able to upload a specially crafted file that would result in the execution of embedded code.
Threat actor interest in this critical severity vulnerability began immediately following its disclosure on 23 Sep 2021, which was likely sparked by an incomplete proof of concept released by a researcher. The researcher claimed that the PoC—which was reportedly based on the workaround and patch that VMWare released—could be used by experienced developers to create a working exploit but would not be sufficient for lesser-skilled actors. However, a working exploit for CVE-2021-22005 was quickly established on 27 September. Cybercriminal discussions of methods to use the working exploit were identified in late December 2021; the two users highlighted in the image below discuss using standard commands to change passwords and add users on susceptible systems.
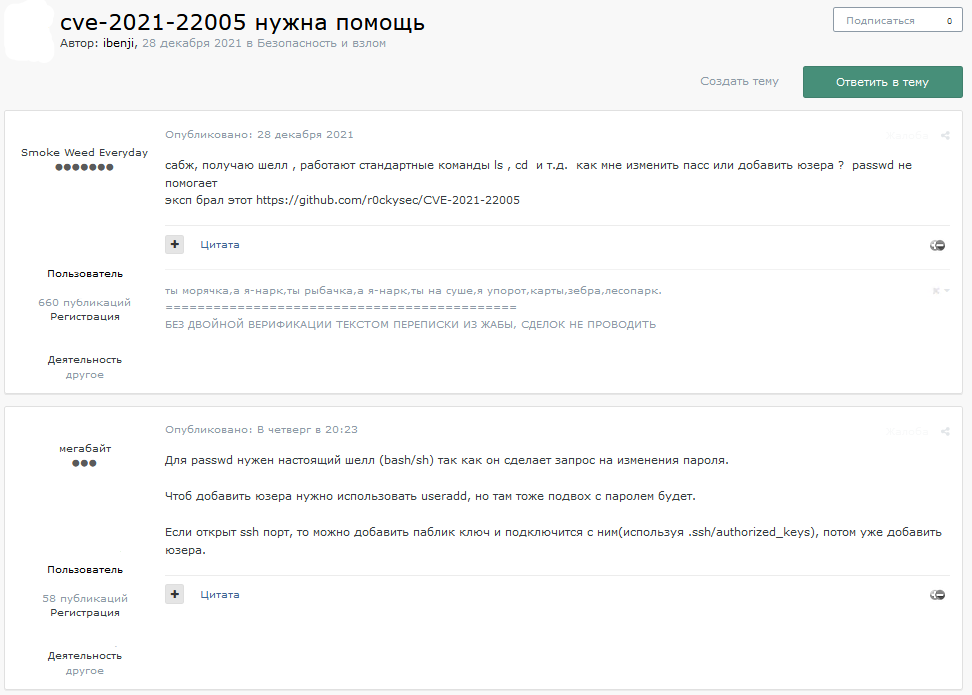
CYBERCRIMINAL POSTS RELATED TO CVE-2021-22005
The rapid increase in risk associated with this vulnerability adds fuel to the ongoing debate over whether security researchers should publish PoCs before organizations have had time to issue a patch. In June 2021, Github—which is now under the ownership of Microsoft—changed their policy to permit the removal of such items, which would minimize the risk of the exploits being used in live attacks. Microsoft will likely point to examples like CVE-2021-22005 when demonstrating that the public issue of even incomplete PoCs can quickly fall into the hands of malicious actors.
MAKING VULNERABILITY INTELLIGENCE WORK FOR YOU
As we’ve highlighted in this blog, vulnerability intelligence can be an incredible asset for fine-tuning your vulnerability management process. By understanding the context behind individual vulnerabilities, security teams can move away from solely using CVSS scores and instead focus on what matters to your organization. Too many vulnerabilities and far too little time are common sentiments among the security community; at Digital Shadows, we pride ourselves in allowing our clients to reduce the noise and focus on what matters. Taking a risk-based approach is the most effective method of targeting vulnerabilities, which will ultimately have the most significant impact on reducing your overall cyber risk.
You may also enjoy reading, The largest DDoS to date, Microsoft mitigates a 3.47 Tbps DDoS attack
Stay informed of the latest Cybersecurity trends, threats and developments. Sign up for RiSec Weekly Cybersecurity Newsletter Today
Remember, CyberSecurity Starts With You!
- Globally, 30,000 websites are hacked daily.
- 64% of companies worldwide have experienced at least one form of a cyber attack.
- There were 20M breached records in March 2021.
- In 2020, ransomware cases grew by 150%.
- Email is responsible for around 94% of all malware.
- Every 39 seconds, there is a new attack somewhere on the web.
- An average of around 24,000 malicious mobile apps are blocked daily on the internet.




