Internet access is no longer an option; it has become a requirement for everyone. Internet connection has its own set of advantages for an organization, but it also allows the outside world to communicate with the organization’s internal network.
Visiting another website requires connection to a specialized computer called a web server, which, like any other computer, can be targeted by hackers. Attackers have the potential to infect the host computer with malware and start DDoS attacks when they connect to a foreign machine.
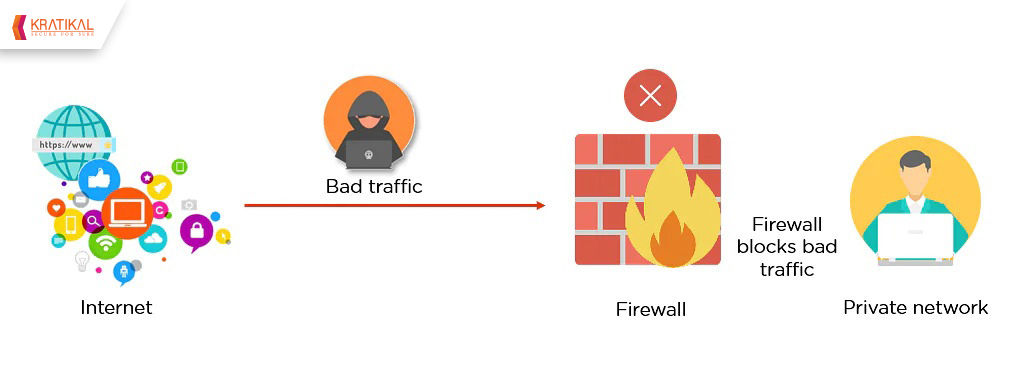
That is where a firewall becomes helpful.
What is Firewall?
A firewall is a type of network security device that monitors and controls incoming and outgoing traffic. It can be either hardware or software. It allows, rejects, or blocks specific traffic based on a predetermined set of rules. It protects the network from both external and internal threats.
How does a firewall work?
When encountering unauthorized traffic, a firewall runs a scan and tries to match the traffic with its defined set of rules. Once the network matches with the set of rules, appropriate actions are taken for that specified network. If the incoming traffic is determined to be a security risk, the firewall prevents it from entering the internal network.
The vulnerability of networks connected to the internet necessitates the use of firewalls. A third party can readily infiltrate and infect an unprotected network. The hacked website or server might be infected with malware once the hackers gain control of it. DDoS (Distributed-Denial-of-Service) attacks, which can force a website or server to crash, can render your network vulnerable if firewalls aren’t installed.
There are different ways a firewall can filter and control the unauthorized traffic, such as:
- Packet Filtering
In this strategy, packets are formed up of little pieces of data that are treated separately by firewalls. Packets trying to enter the network are checked against a set of rules. The packets that match a known threat are quarantined, while the others are allowed to proceed to their intended destination.
This form of firewall has no way of knowing if the packet is part of an existing traffic stream. Packets can only be allowed or denied depending on their unique headers.
- Stateful Inspection
Stateful Inspection is a more advanced type of firewall filtering that looks at a variety of elements in each data packet and compares them to a database of reliable data. The source and destination of IP addresses, ports, and applications are among these factors.
To be allowed to get through to the internal network, incoming data packets must have the required information.
- Proxy Service
To safeguard network resources, the Proxy Firewall, also known as an Application Firewall or a Gateway Firewall, inspects incoming traffic at the application layer. It restricts the kind of applications that a network can support, which improves security but reduces functionality and performance.
A proxy server acts as a go-between, preventing direct connections between the two sides of the firewall. Each packet must pass via the proxy, which determines whether traffic is allowed to pass or is blocked based on the rules set forth.
- Next Generation Firewalls (NGFW)
Next-generation firewalls (NGFWs) are used to guard against modern security threats such as malware and application-layer assaults. Packet Inspection and Stateful Inspection are combined in NGFW. To protect the network from modern threats, it also contains Deep Packet Inspection (DPI), Application Inspection, malware filtering, and antivirus.
The Importance of proper Firewall Configuration
A firewall is an important part of network security and must be configured correctly to protect a company against cyberattacks and data breaches. Hackers can obtain unauthorized access to a protected internal network and steal critical information if the firewall is configured incorrectly.
A properly configured firewall can protect an online server from harmful cyberattacks to the fullest extent possible.
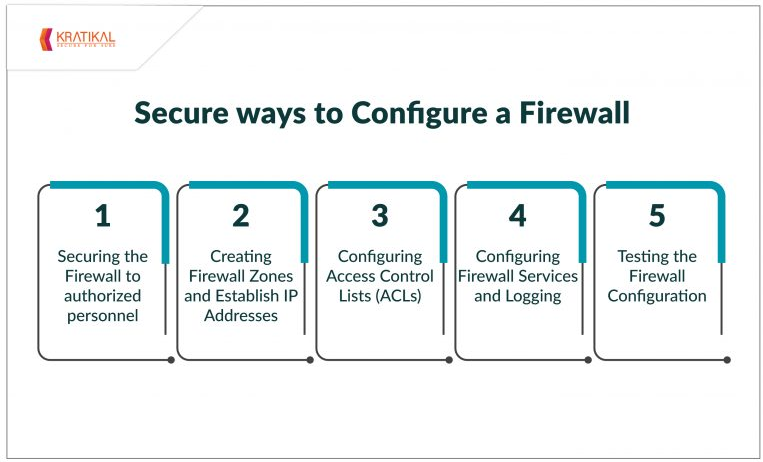
Secure ways to Configure a Firewall
Firewall setting is critical for ensuring that only authorized administrators have access to a network.
The following actions are required:
- Securing the Firewall to authorized personnel
Secure your firewall so only authorized personnel can access the internal network.
- Update your firewall to the latest firmware.
- A firewall should never be put into production without the proper configurations in place.
- Delete, disable, or rename the default accounts and use unique and complex passwords.
- Never use shared accounts managed by multiple administrators.
- Disable Simple Network Management Protocol (SNMP).
- Creating Firewall Zones and Establish IP Addresses
Decide which assets need to be safeguarded and map out your network so that these assets can be grouped together and assigned to different networks or zones based on their functions and sensitivity levels. The greater the number of zones you construct, the more secure the network will be.
However, managing more zones takes more effort, which is why assigning zones to firewall interfaces and sub interfaces requires establishing associated IP addresses.
- Configuring Access Control Lists (ACLs)
Access Control Lists are used by organizations to determine which traffic is permitted to pass or is banned (ACLs). ACLs are the rules that a firewall uses to determine what actions should be taken in response to unauthorized traffic attempting to access the network.
The actual source and destination port numbers as well as IP addresses should be specified in ACLs. Each ACL should have a “Deny All” rule to allow organizations to filter traffic. The interface and sub interface should both be inbound and outgoing to guarantee that only allowed traffic reaches a zone.
- Configuring Firewall Services and Logging
Other services, such as an Intrusion Prevention System (IPS), a Network Time Protocol (NTP) server, and others, can be built within some firewalls. It’s critical to turn off any firewall-supported extra services that aren’t in use.
- Testing the Firewall Configuration
It’s crucial to test your firewall settings once you’re confident it’s correct. Testing such as Vulnerability Assessment and Penetration Testing (VAPT) is crucial for ensuring that the correct traffic is permitted to pass and that the firewall is working as intended. In the event that the firewall configuration fails during the testing phase, make a backup.
HOW KRATIKAL CAN HELP?
As a CERT-In empanelled cybersecurity solutions firm, Kratikal provides a complete suite of VAPT testing services, one of which is Network Security Testing, a method of evaluating the external and internal security state of a network to detect and illustrate flaws present within the network.
The Infrastructure Penetration Testing includes a variety of tasks like:
- Identifying, prioritizing and quantifying the threats within the network.
- Checking the control of security.
- Analyzing the defenses against network-based attacks such as brute-force attacks, port scanning among the others.
Kratikal also offers Firewall Auditing. The assessment methodology includes proper planning and execution.
The steps followed are:
- Security Configuration Review
- Firewall Rule-set Review or ACL Review
- Firewall Auditing Test Case
- Reporting
Depending on the business and technical requirements, we use industry-standard security testing tools such as Burpsuite, Nmap, Metasploit, and others throughout each IT architecture.
The relevance of firewall setup to the security of our networks cannot be overstated. Firewalls protect our IT infrastructure, but they, too, require regular maintenance in order to perform correctly. A functioning firewall ensures that our networks remain healthy as well.
What other configuration options do you see for a firewall? Let us know what you think in the comments section below!
The post 5 secure ways to configure a Firewall appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Deepti Sachdeva. Read the original post at: https://www.kratikal.com/blog/5-secure-ways-to-configure-a-firewall/
Suggest an edit to this article
Go to Cybersecurity Knowledge Base
Got to the Latest Cybersecurity News
Stay informed of the latest Cybersecurity trends, threats and developments. Sign up for our Weekly Cybersecurity Newsletter Today.
Remember, CyberSecurity Starts With You!
- Globally, 30,000 websites are hacked daily.
- 64% of companies worldwide have experienced at least one form of a cyber attack.
- There were 20M breached records in March 2021.
- In 2020, ransomware cases grew by 150%.
- Email is responsible for around 94% of all malware.
- Every 39 seconds, there is a new attack somewhere on the web.
- An average of around 24,000 malicious mobile apps are blocked daily on the internet.




