The number of Chrome vulnerabilities exploited in malicious attacks has been increasing over the past years and Google believes several factors have contributed to this trend
14 Chrome Zero-Day Vulnerabilities Exploited in Attacks in 2021.
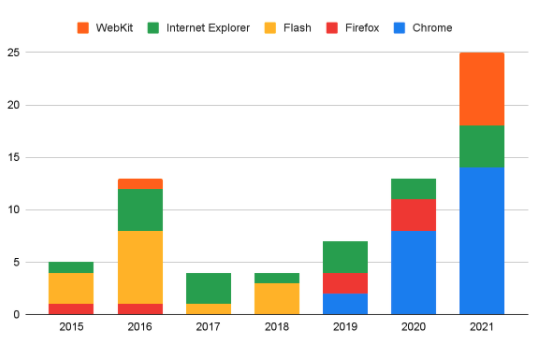
The number of Chrome vulnerabilities exploited in the wild reached 14 in 2021, up from eight in 2020 and two in 2019. Chrome is targeted far more often than Firefox, Safari and Internet Explorer, according to data from Google’s Project Zero research unit, which tracks exploitation of zero-days.
One reason for the increasing number of zero-day attacks targeting Chrome is related to transparency — browser security teams and research groups are increasingly informing the public about in-the-wild exploitation of vulnerabilities. For example, Project Zero’s exploit tracker does not show any Chrome vulnerabilities being leveraged by hackers before 2019, but the internet giant admits that it “doesn’t mean exploitation didn’t happen.”
Another reason for Chrome being increasingly targeted is related to the deprecation of Flash, as well as the web browser’s popularity. Specifically, threat actors often exploited Adobe Flash vulnerabilities in web attacks before the software was killed off, and now they are focusing more on the browser itself. In addition, since the Chromium rendering engine is now also used by Microsoft for its Edge browser, finding a Chromium vulnerability allows attackers to target more systems.
Google has also attributed the rise in the number of exploited Chrome vulnerabilities to the need to chain multiple bugs for a single exploit. Seven years ago, a single vulnerability could be very valuable to attackers, but the security improvements in modern browsers have resulted in a single flaw almost never being enough for an attacker to achieve their goal.
In addition, the company has blamed this trend on the increasing complexity of the browser, which now includes many of the functions of an operating system. This complexity, while beneficial in terms of functionality, also means more bugs.
“Ultimately, we believe data is an important part of the story, but the absolute number of exploited bugs isn’t a sufficient measure of security risk,” Google argued. “Since some security bugs are inevitable, how a software vendor architects their software (so that the impact of any single bug is limited) and responds to critical security bugs is often much more important than the specifics of any single bug.”
The company says it has been taking steps to prevent Chrome from being abused by malicious actors. These steps include faster patching of vulnerabilities and mechanisms designed to make exploitation of entire classes of vulnerabilities more difficult.
Google said recently that it paid out nearly $9 million in bug bounties last year, including roughly $3.1 million for Chrome vulnerabilities.
Only one Chrome vulnerability appears to have been exploited in the wild until now in 2022.
Suggest a change to this article
Go to Cybersecurity Knowledge Base
Got to the Latest Cybersecurity News
Stay informed of the latest Cybersecurity trends, threats and developments. Sign up for our Weekly Cybersecurity Newsletter Today.
Remember, CyberSecurity Starts With You!
- Globally, 30,000 websites are hacked daily.
- 64% of companies worldwide have experienced at least one form of a cyber attack.
- There were 20M breached records in March 2021.
- In 2020, ransomware cases grew by 150%.
- Email is responsible for around 94% of all malware.
- Every 39 seconds, there is a new attack somewhere on the web.
- An average of around 24,000 malicious mobile apps are blocked daily on the internet.




