Our 2021 Website Threat Research Report details our findings and analysis of emerging and ongoing trends and threats in the website security landscape. We’ve put together this analysis to help keep website owners informed and aware of the dangers posed by malicious actors.
This year’s report is a collection of observations made by Sucuri’s Research and Remediation teams from data collected on web-based malware, vulnerable software, and attacks during 2021.
The data used in this report is a representative sample of the total number of websites that our Remediation team performed services for throughout the year 2021, as well as more than 132 million SiteCheck scans. This data reflects the environments of our clients and not the web as a whole. This was a great project to work on and we uncovered a lot of interesting data, particularly with observing trends in credit card skimming malware and WordPress. Some trends from previous years continued while some fresh ones emerged. Our hacked website report contains a lot of new data, including sections on emerging malware to help us analyze and understand trends in the threat landscape. We also provide an analysis of the most severe and common software vulnerabilities present within the WordPress ecosystem during 2021.
Key Takeaways
- Vulnerable plugins and extensions account for far more website compromises than out-of-date, core CMS files.
- Websites containing a recently vulnerable plugin or other extension are most likely to be caught up in malware campaigns.
- Default configurations of popular website software applications remain a serious liability.
- By default, WordPress administrator panels contain no multi-factor authentication, nor a limit on failed login attempts.
- Responsible disclosure and proactive security monitoring is key to maintaining a safe web.
- Some major catastrophes were avoided in 2021. Major plugins with millions of installations had vulnerabilities patched with very few incidents, due to proactive security monitoring, patching, and exceptional communication with the public.
- Credit card skimming is on the rise, especially for WordPress.
- Hacker groups are actively developing and customizing their malware. Each variation is distributed to a small number of sites, but the overall number of affected sites is significant.
- SEO spam continues to be a menace.
- 52.6% of remediated websites contained some form of SEO spam in 2021. Spam also accounted for 34.45% of infected SiteCheck detections.
- Backdoors and malicious admin users remain the backbone of many compromises.
- Backdoors are extremely common, with 60.04% of infected environments containing at least one website backdoor.
- Website reinfections remain common.
- A website compromise can be a miserable experience. Website owners are often averse to taking all the necessary post-infection steps, but if measures aren’t taken the attackers are likely to return.
- Malware tends to focus on either quality or quantity.
- The goal of spam and redirect malware is to compromise as many websites as possible, in the shortest time period possible, to affect as many users as possible. They do not care about staying hidden. Malware that compromises credit card details is the opposite: They try to have a small, very well hidden payload to stay present as long as possible in order to steal as many card numbers as they can.
- Cryptomining attacks are no longer very common.
- Cryptomining has largely moved away from website and server environments, focusing instead on dedicated hardware “farms”.
Software Distribution
Based on our data, the following graph illustrates the usage of different CMS platforms among our client base.
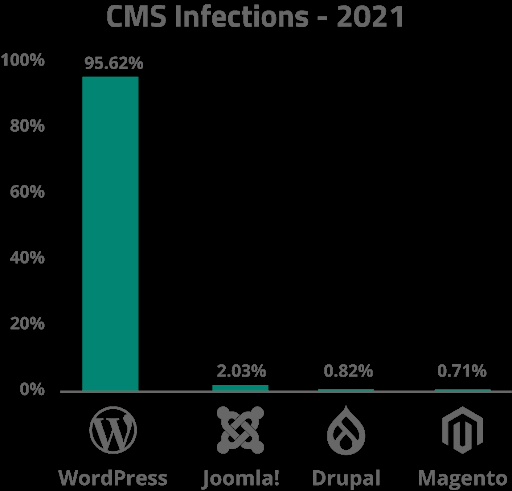
These data sets indicate that WordPress continues to be the most popular CMS among our user base, accounting for 95.62% of clients in 2021. As seen in past years, Joomla (2.03%) followed in second place with Drupal (0.82%) taking third.
Vulnerable Software and Components
Out-of-date CMS
The percentage of websites that had an out-of-date CMS at the time of infection was roughly equal.
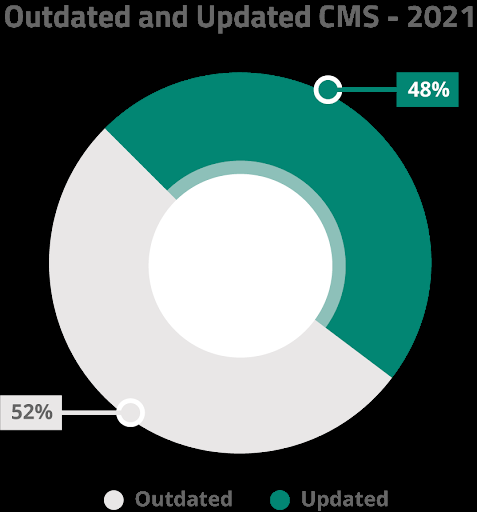
Our data suggests that out-of-date CMS only roughly correlates to infection, and points to the usage of vulnerable plugins and themes as well as unsecured admin panels to be of greater importance in terms of security risk.
The presence of out-of-date CMS may not necessarily be the attack vector itself but rather a symptom of a lack of maintenance of the environment.
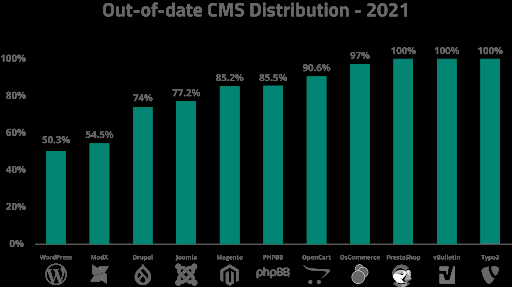
Out-of-date CMS Distribution
Out of all of the websites submitted for malware cleanup, WordPress and ModX were by far the most well maintained at the point of infection.
Top Malware Infections
To identify the most common malware types seen on compromised websites in 2021, our team aggregated and analyzed the data from malware signatures detected and cleaned during Incident Response.
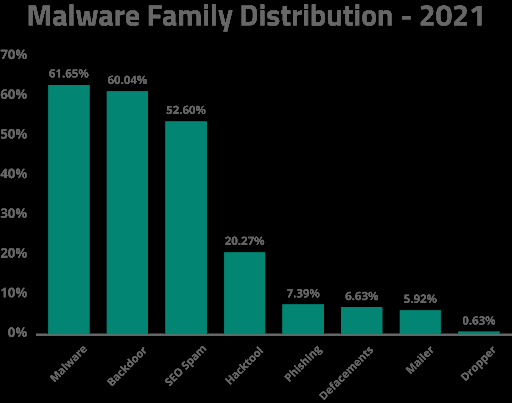
Why is there a percentage overlap? Our teams regularly find multiple types of malware on a compromised website. For example, attackers might infect a website with spam and plant a website backdoor on a website to maintain access to the environment.
Malware
In 2021, 61.65% of remediated websites were flagged with the malware category. Malware is a very broad category which often includes code designed to redirect website visitors to scam and other malicious websites or steal login credentials. It typically engages in some type of malicious action against site visitors, in contrast to backdoors and hack tools that facilitate hacker activities or spam that aims to increase SEO rankings to third party sites.
The top ten most common malware types we cleaned were as follows:
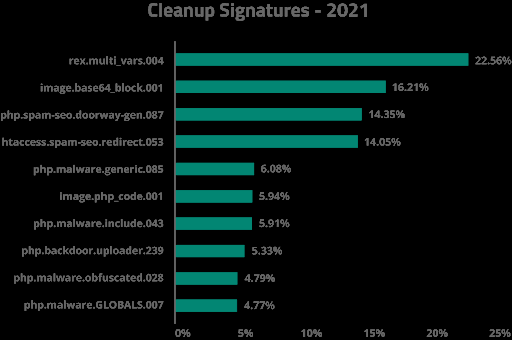
Backdoors
Backdoors were one of the most common threats found on compromised websites in 2021, with 60.04% of all infected sites containing at least one backdoor.
An important tool for attackers, our analysts typically find backdoors alongside many other types of malware. This malware bypasses regular access channels, granting attackers full access to the website backend. Once installed, a backdoor can be used to maintain access to the compromised environment long after the infection has occurred, making it easy for the attacker to reinfect the site after the payload is removed.
We analyzed the different types of backdoors we detected and cleaned in 2021 and found the following distribution.
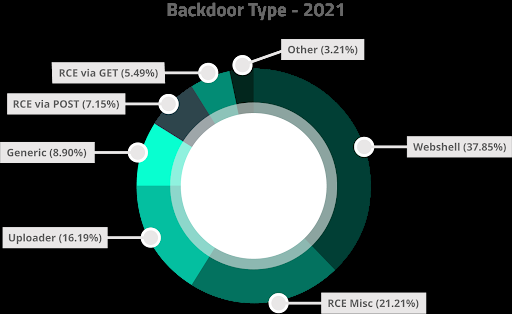
- Uploader
- A type of backdoor which allows the attackers to upload files to the victim environment.
- Webshell
- These backdoors allow the attackers full access to the website file system.
- RCE
- The backdoor will attempt to execute the command issued by the attackers.
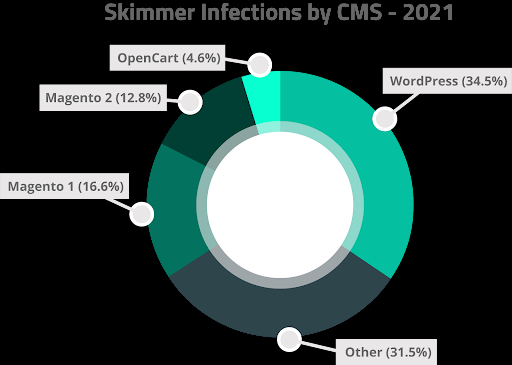
Credit Card Skimmers
Credit card skimmers have increased significantly from previous years and the behavior has become more targeted. A growing number of credit card theft has been occurring on independent websites where the store has set up their own ecommerce website.
Over 25% of all new PHP malware signatures generated in 2021 were for credit card skimmers.
In 2021, SiteCheck detections found that 34.5% of websites infected with a credit card skimmer were running WordPress.
SEO Spam
SEO spam still remains one of the most common website compromises, with 52.6% of remediated websites containing SEO spam. Infections typically occur via PHP, database injections, or .htaccess redirects.
SEO attacks often infect websites with redirects and spam, referring site visitors to spam landing pages. These attacks can significantly impact rankings and organic traffic from popular search engines like Google, Bing, and Yahoo who block websites with malicious content.
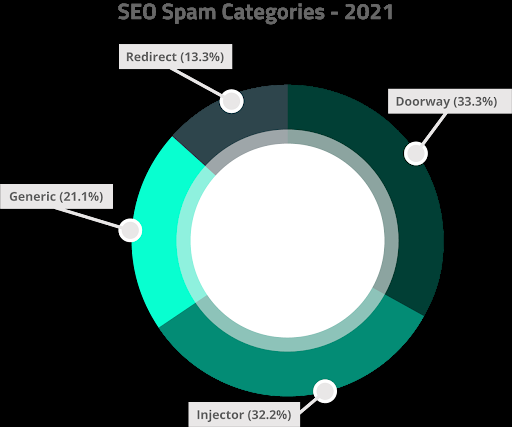
Our analysis revealed that 33.3% of SEO spam infections were spam doorways, which produce subsections of dynamic spam content on a compromised website. Another 32.2% of SEO spam infections were related to spam injectors, responsible for peppering a compromised environment with hidden spam links for SEO purposes.
Unsurprisingly, our analysis revealed that the most common SEO spam themes and keywords on compromised websites included pharmaceuticals like Viagra and Cialis.
Top Spam Themes
- Pharmaceuticals
- Essay writing services
- Knockoff jerseys and other brand name products
- Escort services
- Adult websites
- Online casinos
- Replica watches
- Pirated software
Left untreated, SEO spam can seriously damage a website’s reputation and take a significant time to recover. Website owners may experience a loss in revenue, hijacked search results, browser warnings, or even blocklisting.
Phishing
Phishing has become more prevalent in recent years, with 7.39% of websites containing some form of phishing in 2021. By and large what we see are legitimate websites hacked to host phishing content. This distances the attacker from their payload and allows them to avoid culpability and lower their costs.
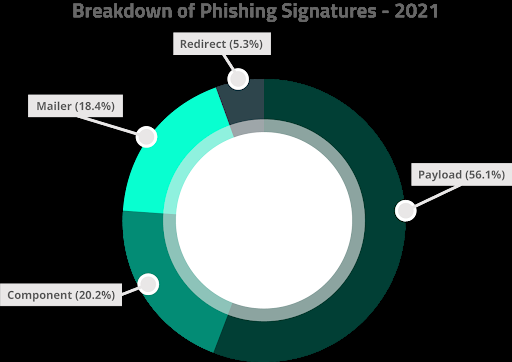
Phishing tends to target login credentials for cloud services such as Microsoft Office and Adobe, as well as financial institutions and popular services such as Netflix. Stolen passwords are also used in credential stuffing attacks. The majority of phishing were payloads (phishing landing pages) targeting a wide variety of companies and services. A large portion of attackers used ready-made, pre-built phishing kits and installed them onto their targets. These kits contain some key component parts:
- A payload landing page
- A mailer script to either send the compromised data to the attackers or to send out phishing emails to victims
- Code designed to prevent search engines from indexing the payload
SiteCheck and Blocklist Analysis
Our SiteCheck tool is one of our most important website security monitoring tools. It is free to use and scans millions of websites per year.
Since it is an external monitoring tool, it cannot see infections that do not display outwardly on websites (such as PHP backdoors). For a comprehensive solution, Sucuri clients have full access to our server-side scanning and monitoring.
We queried the scans performed on SiteCheck during 2021 to identify the trends seen for our remote security scanner.
From the 132,374,781 scans performed with SiteCheck in 2021, a whopping 10.38% of websites were identified as containing out-of-date software and 4.34% were identified as infected. Of these infected websites, 34.45% had been identified as containing SEO spam while less than 1% were website defacements.
Blocklisted Domains
Within the top blocklisted resources, we found a number of domains related to the massive WordPress campaign our team has been tracking for several years.
This campaign largely aims to redirect users to spam, malware and scam sites. Nearly all of the domains listed below were present in siteurl/home database infections or in injections targeting wp_post content in WordPress environments.
To dig a bit deeper, we analyzed the top blocklisted resources for this ongoing campaign.
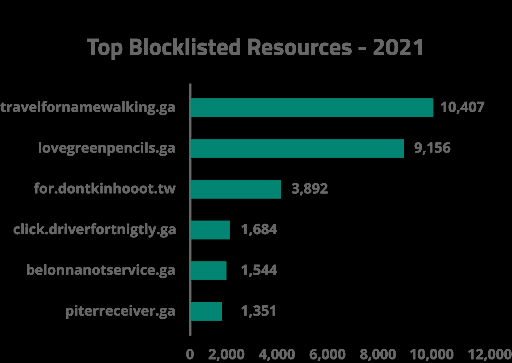
One prevalent theme that differed from previous years was the high prevalence of .ga (Gabon) and .tw (Taiwan) domains used in redirect campaigns. These top-level domains have become very popular among attackers due to lack of active regulation and domain ownership restrictions.
Spam
SEO spam accounted for 34.45% of the infected websites scanned with SiteCheck in 2021. Since this number was so significant, we dug a bit deeper to break down the types of spam found on these compromised environments.
Our analysis of the top ten SEO spam signatures for SiteCheck revealed a few prevalent themes.
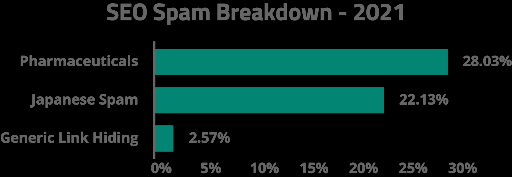
Unsurprisingly, the most common theme was related to pharmaceuticals with 28.03% of SEO spam content found to be related to themes like Viagra and Cialis. This indicates that despite the long legal battles fought by pharmaceutical companies against spammers, knock-off drugs continue to be an important source of revenue for attackers.
A predominant number of signatures were also found relating to Japanese SEO spam (22.13%). These ongoing SEO Japanese Spam campaigns pollute victim’s website search results with knock-off designer goods.
Conclusion
At its core, maintaining a good security posture comes down to a few core principles: keep your environment updated and patched, use strong passwords, exercise the principle of least privilege, and leverage a web application firewall WAF to filter malicious traffic.
Check out the full hacked website report to get the entire story on our 2021 research and remediation analysis!
Download the full report (hosted by sucuri.net)
Suggest an edit to this article
Go to Cybersecurity Knowledge Base
Got to the Latest Cybersecurity News
Stay informed of the latest Cybersecurity trends, threats and developments. Sign up for our Weekly Cybersecurity Newsletter Today.
Remember, CyberSecurity Starts With You!
- Globally, 30,000 websites are hacked daily.
- 64% of companies worldwide have experienced at least one form of a cyber attack.
- There were 20M breached records in March 2021.
- In 2020, ransomware cases grew by 150%.
- Email is responsible for around 94% of all malware.
- Every 39 seconds, there is a new attack somewhere on the web.
- An average of around 24,000 malicious mobile apps are blocked daily on the internet.




