A new threat has surfaced that could potentially impact millions of GitHub repositories. Known as RepoJacking, this attack could execute code on the internal networks of organizations or even on the networks of their customers. In fact, this includes the repositories of big-name companies like Google and Lyft. In this blog post, we’ll discuss the implications of RepoJacking, how it works, and what you can do to safeguard your repositories.
Understanding the Extent of the Threat
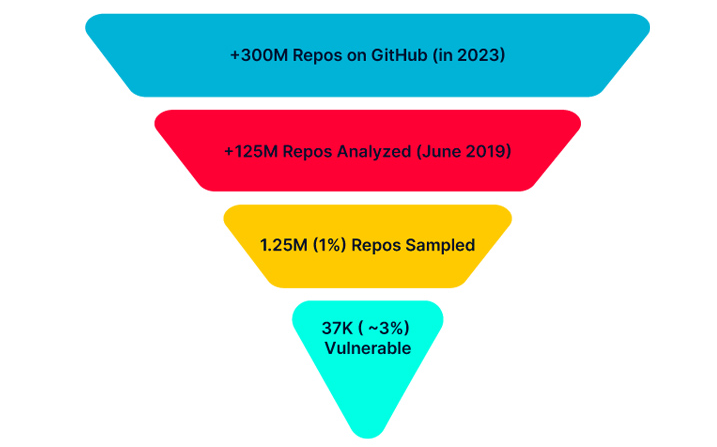
According to a study conducted by AquaSec’s security team, “Nautilus,” approximately 2.95% of the 1.25 million GitHub repositories examined were vulnerable to RepoJacking. To put that into perspective, if we extrapolate these findings to all of GitHub’s 330 million repositories, potentially millions of repositories may be susceptible to a similar assault.
How Does RepoJacking Work?
To understand RepoJacking, it’s crucial to know what happens when a GitHub repository changes its name. This might occur because a company decides to adopt a new brand name, or when companies merge or get acquired, resulting in new management. When a repository’s name changes on GitHub, a redirection is created to prevent code from renamed repositories from breaking dependencies. However, if a hostile actor registers the previous name, they can render the redirection invalid.
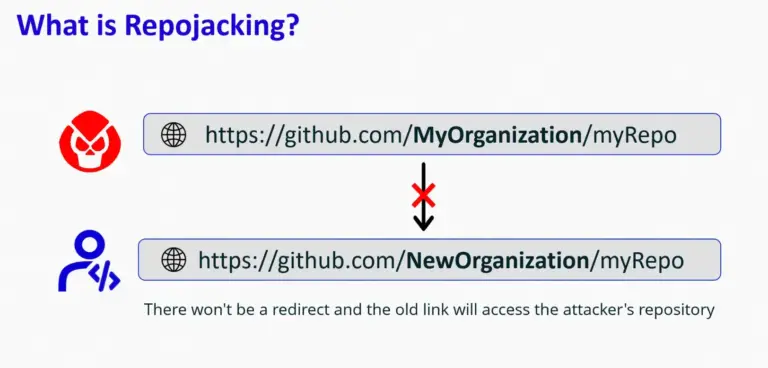
The attacker can then control the repository. Consequently, any code or project that depends on the attacked project’s dependencies will retrieve those dependencies and other code from the attacker-controlled repository. This code may include malware.
This situation could also occur if control of a repository is transferred to another user and the original account is deleted. This allows an attacker to create an account with the old username, thereby gaining control over the repository.
Threat actors can identify unique repositories using services like GHTorrent, which harvests GitHub metadata linked to public commits and pull requests.
An example of this is the Google/mathsteps repository, formerly owned by Socratic (socraticorg/mathsteps), a company that Google acquired in 2018. If an attacker were to open the socraticorg/mathsteps repository, users following Google’s instructions would clone the attacker’s repository instead, leading to arbitrary code execution on the user’s systems.
The Current State of GitHub’s Safeguards
GitHub has implemented certain safeguards against RepoJacking attacks. However, these measures appear to be insufficient and relatively easy to bypass. For instance, GitHub only protects the most well-known projects, leaving the lesser-known, more vulnerable projects that depend on them exposed to the supply chain breach.
Moreover, when a repository’s name is changed and GitHub protects it with over 100 clones, it seems like a sign of malicious planning. This protection does not cover projects that gained popularity after changing their name or changing ownership.
Mitigating the Threat
As a first line of defense, it’s crucial to regularly check your repositories for any links that might pull resources from external GitHub repositories. This is because projects like Go modules could change their names at any point. If you notice a name change in a project you depend on, make sure you are pulling from the correct, updated repository.
If your company changes its name, make sure you still own the previous name—even if it’s just a placeholder. This prevents potential intruders from registering and using it for malicious purposes.
RepoJacking is a real and present threat to millions of repositories on GitHub. Awareness of this attack and implementing the suggested mitigation strategies can significantly reduce your vulnerability and ensure the security of your repositories.
See the post from AquaSEC: https://blog.aquasec.com/github-dataset-research-reveals-millions-potentially-vulnerable-to-repojacking
Suggest an edit to this article
Check out our new Discord Cyber Awareness Server. Stay informed with CVE Alerts, Cybersecurity News & More!
Remember, CyberSecurity Starts With You!
- Globally, 30,000 websites are hacked daily.
- 64% of companies worldwide have experienced at least one form of a cyber attack.
- There were 20M breached records in March 2021.
- In 2020, ransomware cases grew by 150%.
- Email is responsible for around 94% of all malware.
- Every 39 seconds, there is a new attack somewhere on the web.
- An average of around 24,000 malicious mobile apps are blocked daily on the internet.




