TellYouThePass ransomware has re-emerged as a Golang-compiled malware, making it easier to target more operating systems, macOS and Linux, in particular.
The return of this malware strain was noticed last month when threat actors used it in conjunction with the Log4Shell exploit to target vulnerable machines.
Now, a report from Crowdstrike sheds more light on this return, focusing on code-level changes that make it easier to compile for other platforms than Windows.
Why Golang?
Golang is a programming language first adopted by malware authors in 2019 due to its cross-platform versatility.
Furthermore, Golang allows lining dependency libraries into a single binary file, which leads to a smaller footprint of command and control (C2) server communications, thus reducing detection rates.
It is also easier to learn than other programming languages, e.g. Python, and features modern debugging and plugin tools that simplify the programming process.
A notable example of a successful malware written in Golang is the Glupteba botnet, which was disrupted last month by Google’s security specialists.
New TellYouThePass samples
Crowdstrike analysts report a code similarity of 85% between the Linux and Windows samples of TellYouThePass, showcasing the minimal adjustments needed to make the ransomware run on different operating systems.
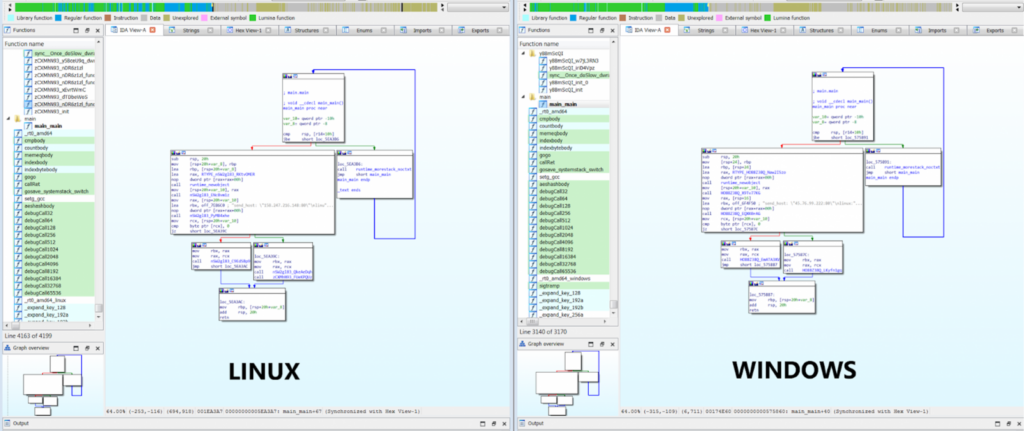
Source: Crowdstrike
One noteworthy change in the latest samples of the ransomware is the randomization of the names of all functions apart from the ‘main’ one, which attempts to thwart analysis.
Prior to initiating the encryption routine, TellYouThePass kills tasks and services that could risk the process or result in incomplete encryption, like email clients, database apps, web servers, and document editors.
Moreover, some directories are excluded from encryption to prevent rendering the system non-bootable and thus waste any chance to get paid.
The ransom note dropped in the recent TellYouThePass infections asks for 0.05 Bitcoin, currently converting to about $2,150, in exchange for the decryption tool.
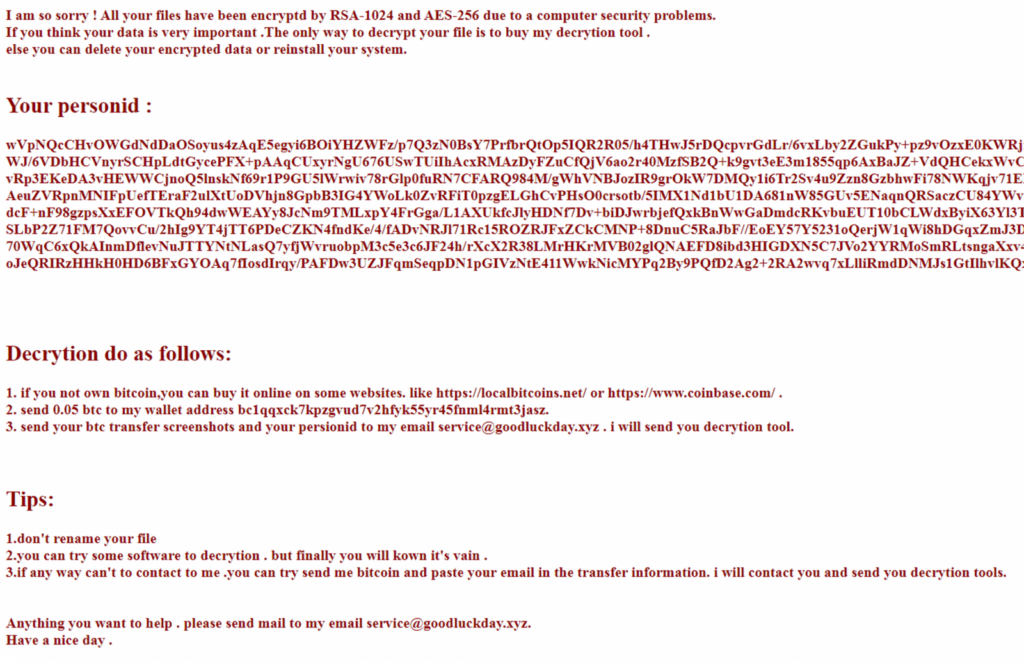
Source: Crowdstrike
The encryption scheme uses the RSA-2014 and AES-256 algorithms, and there is no free decryptor available.
For the time being, macOS samples have not been spotted.




