Identity theft has taken on a whole new life in the digital age and our data has become a valuable commodity that can be monetised and used to commit fraudulent activities.
Data breaches are happening on an almost daily basis and Identity theft is the main driver behind all attacks, accounting for 65% of breaches and over 3.9 billion of the compromised data records this year.
It’s become a big business that’s costing the global economy an estimated £3.2 trillion a year and according to recent research from Cifas, the number of identity theft victims has risen by 57% in the last year alone.
If criminals can get hold of your name, address, phone number or banking details, they can then use this information to steal your identity and commit fraud. Typically, this information will be used to open accounts, apply for loans, or they may even try to obtain a driving licence or passport using this stolen data.
Criminals may be able to gather a large amount of this information from bank statements or paper documents, but increasingly the easiest way for them to gain access to this priceless data is by going online.
It’s unbelievable how much information the criminals can extract from social media platforms or how easy we make it to break into our accounts by choosing passwords that could be hacked within minutes.
Tips To Prevent Identity Theft
Thankfully there are a number of steps you can take to keep your data safe and prevent identity theft.
1. Use strong passwords

Creating a strong password is the first line of defence in preventing identity theft. One of the easiest ways for criminals to hack into your accounts and steal personal and financial information is to guess passwords. If they can successfully crack the password for just one of your accounts, there’s a good chance they can hack multiple accounts using the same details.
A strong password should be between 8-15 characters long, a mix of uppercase and lowercase letters and include numbers or symbols. For extra security, a passphrase can be created which is a password composed of a sentence or combination of words. The first letter of each word will form the basis of the password and letters can be substituted with numbers and symbols to make it more difficult to crack.
Lets give an example of good V bad passwords.
Corrupted100 – BAD
Corrupted123 BAD
LondonJohn100 BAD
not!C0rupt3d!()()%!100! GOOD
C0rupt3d!RiSec%!100! GOOD
L0Nd0n$John!1$0%0! GOOD
Okay – you got the idea – avoid dictionary type passwords, real world names, patterns. Use symbols in replacement of letters, symbols to follow letters etc. At the very least you should aim to have symbols at the beginning or end of your password. Passwords that don’t require any effort in memorizing are always a bad idea.
2. Check ALL social media privacy settings

Social Media is great for catching up with friends however by oversharing online, you can put yourself at great risk of identity theft or even a home burglary. Criminals can collect a huge amount of data about you from your social media profiles.
Whether you’re on Instagram, Facebook, Twitter or LinkedIn, check the site’s privacy policy and use security and privacy settings to control who can see your personal information. Be careful who you accept friend requests from and try not to share too much information that could reveal where you live, when you’re away on a holiday or any other personal data that could compromise your identity.
3. Avoid phishing emails online
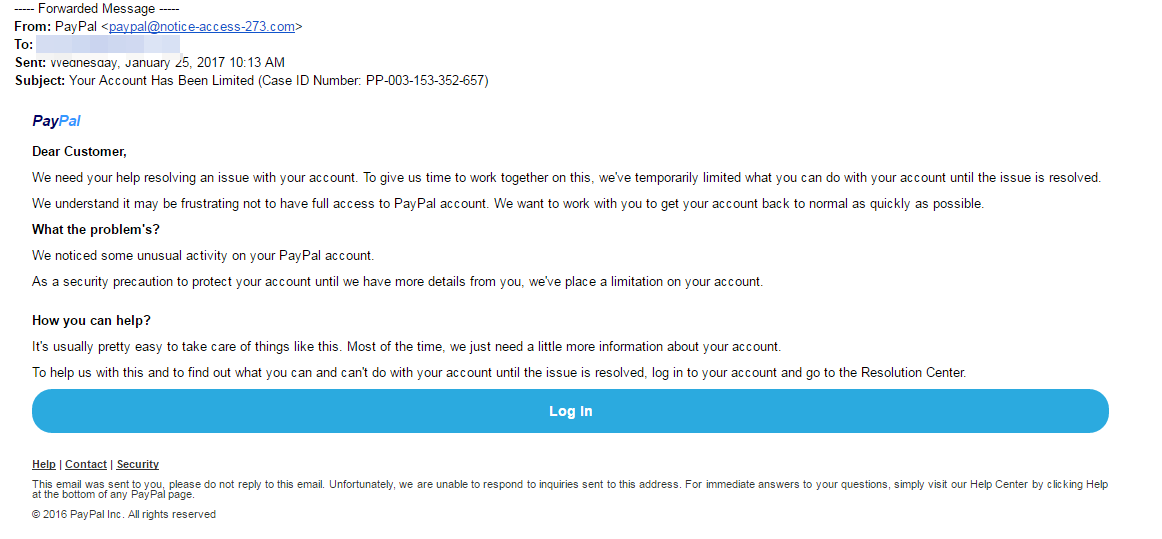
The above example is of course fake. Just look at the “From” It may say PayPal.. but look further, look at the replyto address, look at the from address.
Phishing continues to be one of the most popular ways for criminals to steal personal information and commit identity fraud.
Phishing emails are carefully designed to trick you into entering confidential information such as an account number, password or date of birth by clicking on a link. The email may also include an attachment that once opened will directly infect your computer with malware.
Despite appearing legitimate, there are often a number of red flags that may point to a phishing email. These include: a mismatched URL, poor spelling and grammar, requests for sensitive information, unexpected correspondence and the use of threatening or urgent language.
4. Avoid all public Wi-Fi where possible
This is probably one of the least noted issues with privacy and or ID theft.
There’s no doubt that using public Wi-Fi is a quick, convenient, and free way to go online, however, it opens us up to a range of security risks that can ultimately lead to identity theft.
Public Wi-Fi requires no authentication to establish a network connection, allowing criminals direct access to any unsecured devices on the same open network. Unsecured Wi-Fi networks may also be used to spread malware allowing criminals unrestricted access to everything on your device. This information can, in turn, be used to commit identity fraud, or the information can be sold on to criminal third parties.
5. Check all bank statements regularly
It’s worth keeping a close eye on bank statements to make sure there are no unusual transactions on your account. To avoid detection, criminals will often make few initial debits for smaller amounts, then make a much larger debit which could ultimately clean out your bank account. If you notice any suspicious activity on your account, you should report this to your bank or financial services provider immediately.
6. Always use secure websites
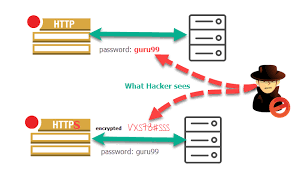
The easiest way to check if the site you are on is secure is to check the URL. At the start of all web addresses, you will see either a ‘http’ or a ‘https’. Always use a site that starts with https as the ‘s’ stands for secure and ensures that all communication between your browser and the website you are visiting is encrypted. This system is not totally foolproof but it will add an extra layer of security and reduce the chance of your data falling into the wrong hands.
7. Ensure AV security software is kept up to date
The installation of anti-virus software will help detect threats on your computer and block unauthorised users from gaining access. It’s also important to ensure that your software is regularly updated to prevent cybercriminals from gaining access to your computer through vulnerabilities in older and outdated systems. Regular software updates will ensure that you have the most up to date versions released by the manufacturer, thereby reducing your chance of attack.
8. Shred sensitive documents

Your personal information is what identity thieves are after and gaining access to the paper copies of your bank statements, payslips or any other mail that may contain personally identifiable information is one of the easiest ways for them to steal this data. Always shred and properly dispose of any sensitive information to ensure it can’t be used to identify you and commit fraud.




